IT Management should not be complicated – get Managed Help Desk Services
An IT system that has never faced a crash, downtime, or an operational issue is only a myth. Several people across the globe go through IT issues daily and are...
Surviving the biggest threat of the year – Ransomware
Only when you thought you did nothing more than clicking on a web link, your files are encrypted and locked, and you can't access your data. This is a painful...
Scaling & Adapting Operation Model for Rapid Business Growth
ExterNetworks' Chief Marketing Officer & President Offers Valuable Insights on Scaling & Adapting Operation Model for Rapid Business Growth ExterNetworks was awarded the prestigious '2016 NEW JERSEY FUTURE 50 SmartCEO...
How to Choose the Best Cloud MSP for Beneficial Cloud Adoption
Technology-enabled services in an on-demand, cost-effective, secure, and quick manner are a must in today's business landscape. The need for such a service at will has given rise to the...
Using IoT Data to Generate Recurring Revenue Opportunities
The Internet of Things (IoT) has been forecast to be larger and more significant than the emergence of laptops, mobiles, and tablets, all put together. However, in spite of the...
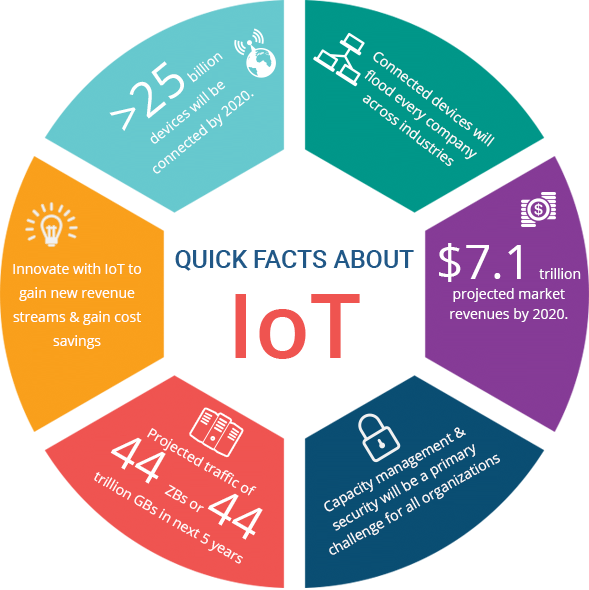
Internet of Things (IoT) Trivia 2
Do you know enough about IoT? It's time to test your knowledge on the total market potential of the IoT, how swiftly IoT is growing, how much money businesses are...
Your Company’s Firewall Security is Vulnerable to Hacking
One of the great intrigues in security management is the modus operandi of criminal hackers. Many organizations believe they are too small a target for hackers to attack. Earlier, cyber...
Internet of Things (IoT) Trivia
Do you know enough about IoT? It's time to test your knowledge on the total market potential of the IoT, how swiftly IoT is growing, how much money businesses are...
Unexpected Cloud Challenges that CIOs Encounter
Cloud technology has transformed the way businesses run and so far companies that have adopted cloud have gained scalability, flexibility, optimum use of IT resources, reduced operational cost, and much...
Managing The IoT’s Inherent Challenges for Business Success
The IoT presents various opportunities to make systems more efficient in helping people make better decisions and improve their quality of lives. The IoT has ‘connected things', such as machines,...
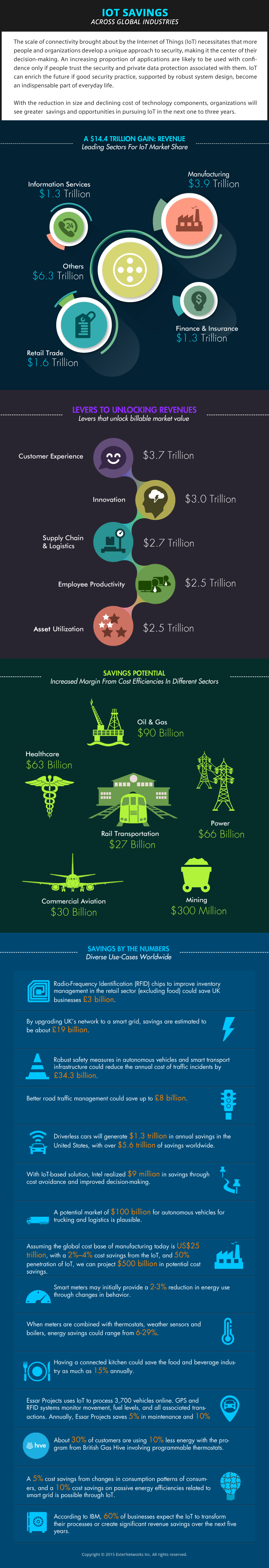
IoT Savings Across Global Industries -Infographic
The IoT connects computer networks, machines, actuators, sensors, and devices globally; and blends the physical world with the virtual world of the Internet and software. It enables companies and consumers...
Preventing Cyber Attacks Through Efficient Cyber Resilience
Today's business world requires companies to use a broad range of technology and IT equipment, the Internet, as well as mobile devices for conducting business. Hence, it is natural that...
Is Your Anti-virus Giving You a False Sense of Security?
Security management is indisputably important for any company today. Threats to security has led to an inevitable adoption of anti-virus software by most if not all organizations and with good...
Smart Office Needs Smart Security
The Internet of Things (IoT) devices continue to create endless possibilities. Most of all, they have affected our everyday life – the way we eat, sleep, work, live, and commute....
VTech hack Exposed Children’s and Parents’ data
In a recent data breach on a kids toy-maker, VTech, 6.4 million children’s data including photos, first names, genders, birth dates and home addresses, as well as information of...
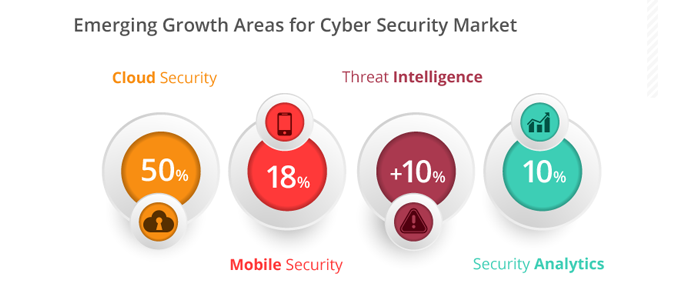
Cyber Security Infographic
Today, every business needs the cyberspace to thrive and the battle to hijack your systems is constant in this realm. Hence, no one is really 100% secure with a...
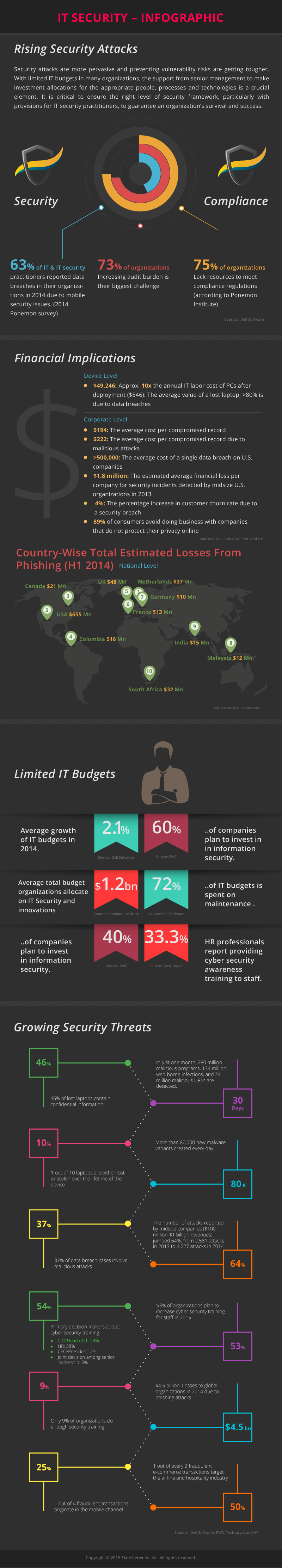
IT Security Infographic
Cyber viruses and IT threat are continuously evolving at this time, when we want to do all things in the cyberspace. It is for this reason that you should always...
Cloud Adoption is Accelerating – Where Do You Stand?
Cloud adoption is no more a matter of if, but what and when. Many organizations have realized and experienced its vast benefits such as business agility, scalability, flexibility, and ROI....
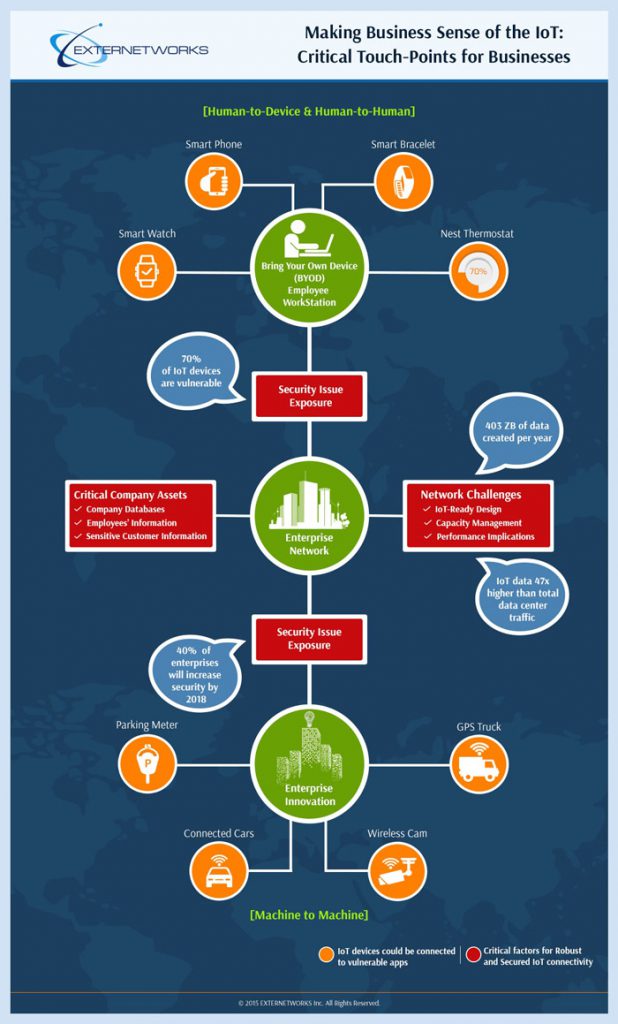
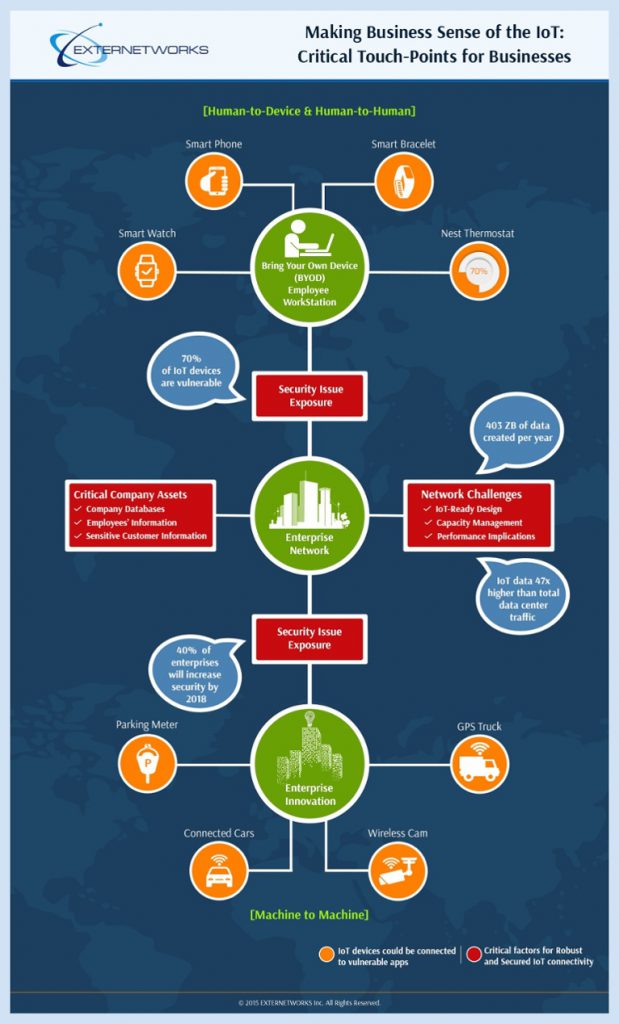
Critical Touch Points of IoT
The Internet of Things (IoT) is fast becoming a household name, as it is the next big area of development in the global technology landscape. Businesses need to take the...
Top and Most Impactful Cyber Attacks in the USA
The exponential rise in cyber attacks and data breaches on big companies has fueled concerns over vulnerable security systems for companies that lost millions of customer’s records to hackers. We’ve...
Attack of the Unknown – Advanced Persistent Threats (APTs)
They’re out there waiting, sitting at their computers hoping for you to make a mistake. And you will, because no one is immune to their advances. It might be an...
Surviving Disaster With Managed Business Continuity Solutions
Globalization has created a highly competitive market for both big and small businesses to thrive. In such competitive times, no business can afford to lose out on opportunities, customers, sales,...
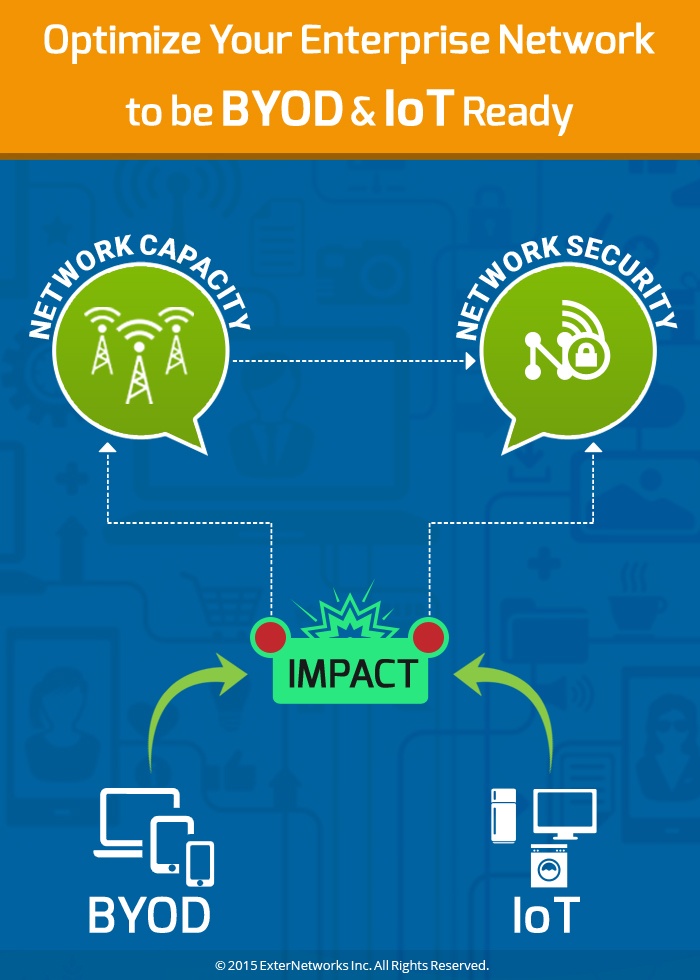
Optimize Your Enterprise Network to be BYOD and IoT-Ready
With the advent of the Internet of Things (IoT) and ‘Bring Your Own Device’ (BYOD) culture, your enterprise network is sure to face a different set of challenges and roadblocks...
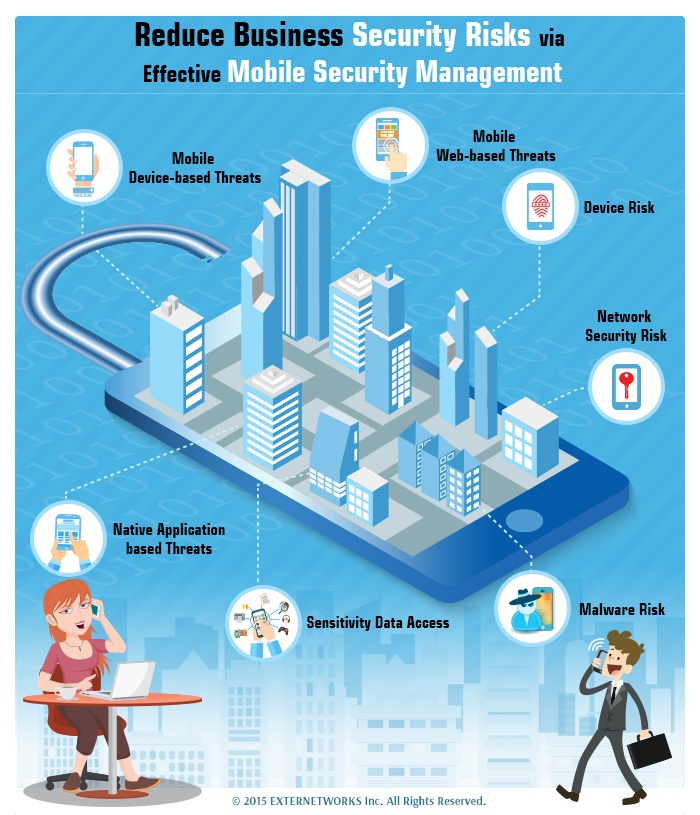
Reduce Business Security Risks via Effective Mobile Security Management
Today, businesses know that they have globally dispersed partners, distributors, and even customers. To keep up pace with the changing conditions of how business is conducted today, more and more...
Data Center Optimization to be IoT-Ready
Technology, which connects everything, has become an inherent part of our lives. These connections have immensely helped organizations to enhance the quality of service to their consumers. As the technology...
Implications of the Internet of Things
With the explosion of connected devices and the massive amounts of data they produce, businesses, individuals, government bodies as well as IT staff need to evaluate their current strategy and...
How to Make Business Sense of the Internet of Things (IoT)
The fundamental need for which a business will adopt new technology is often lost amongst the hype. It can be boiled down to two basic measurable business objectives: To...
Value Proposition and Strategic Partnership through MSP 2.0
Managed Services has seen a tremendous growth in the past three years. Organizations today, whether big or small, have realized the benefits of letting an expert Managed Services Provider (MSP) monitor and...
Adopt Managed NOC as a Comprehensive Solution for Network Operations
Due to technology advancements, organizations now have to integrate many technologies to manage high-performing networks. The complexities of these networks increase and it takes highly specialized tools, resources, process and...
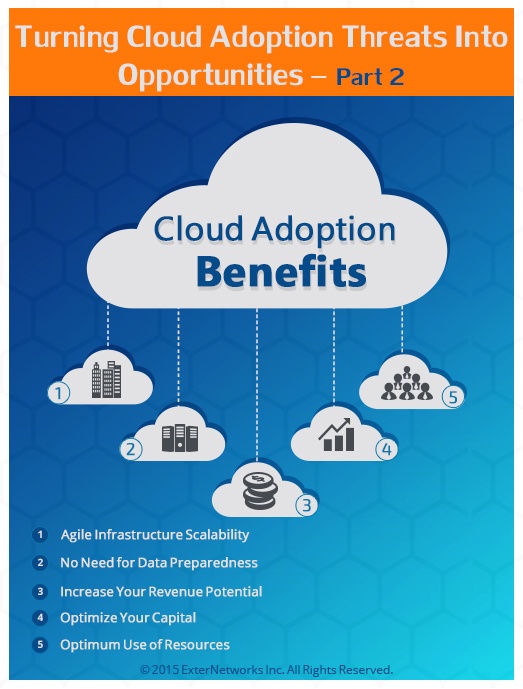
Turning Cloud Adoption Threats into Opportunities (Part 2)
This blog is the second of a two-part series in which we have discussed the challenges and pitfalls of Cloud Adoption and how you can avoid them. In Part 1,...
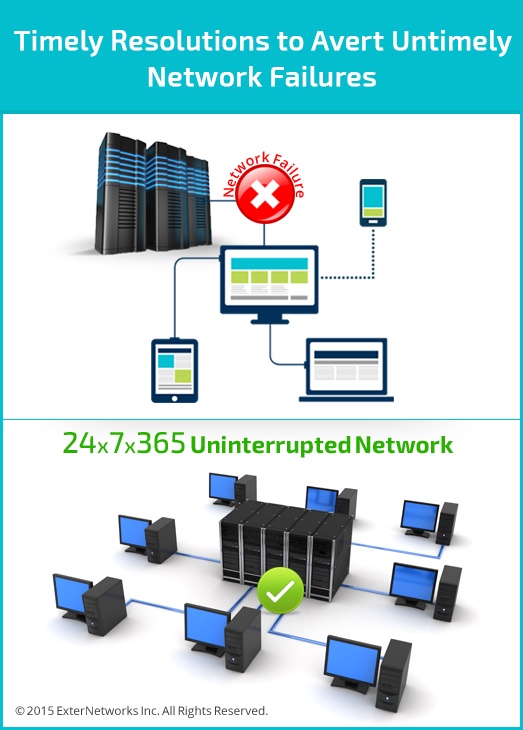
Timely Resolutions to Avert Untimely Network Failures!
Has your network ever experienced untimely network failures? Such untimely network failures can leave any organization, and especially the IT Manager, highly frustrated and helpless. Such failures make you realize...
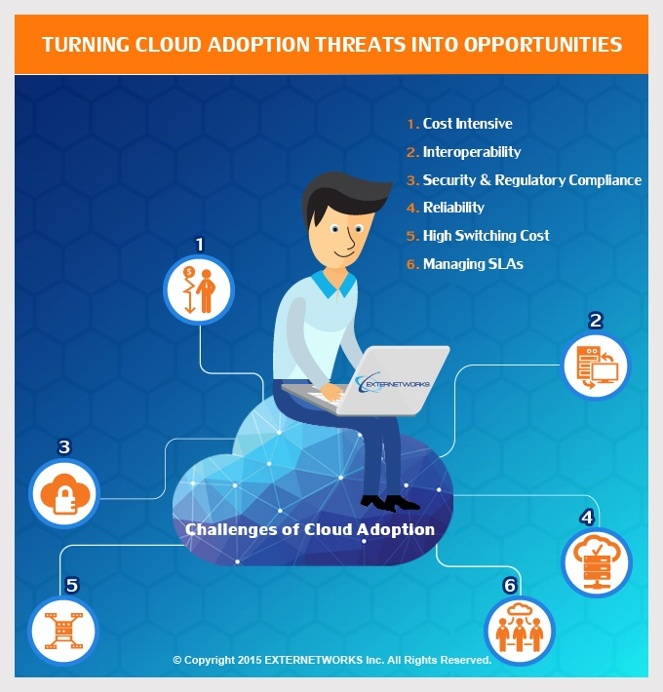
Turning Cloud Adoption Threats into Opportunities (Part 1)
Due to rapid advancements in Cloud technology, its adoption has become more complex, particularly with system integration, data management, and the management of multiple cloud providers. With the increasing complexity,...
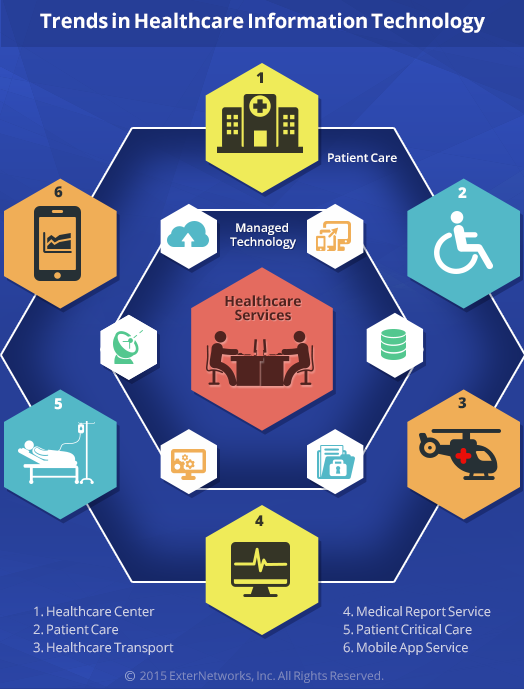
Trends in Healthcare Information Technology that cannot be Ignored
The Healthcare industry has made significant progress over the years by relying on the importance of Technology. Now more than ever, the role of IT plays a crucial role in...
Leverage IoT Technologies to Sustain Competitive Business Advantage
The competition is heating up, as more and more industry giants, such as Google, Samsung, Apple and Microsoft, are entering into the IoT market with large investments to develop their...
Business Continuity Through Managed Network Services (MNS)
If you are a technology manager, you know that we work hard to manage the issues associated with networks. You are at risk every time your company is exposed to...
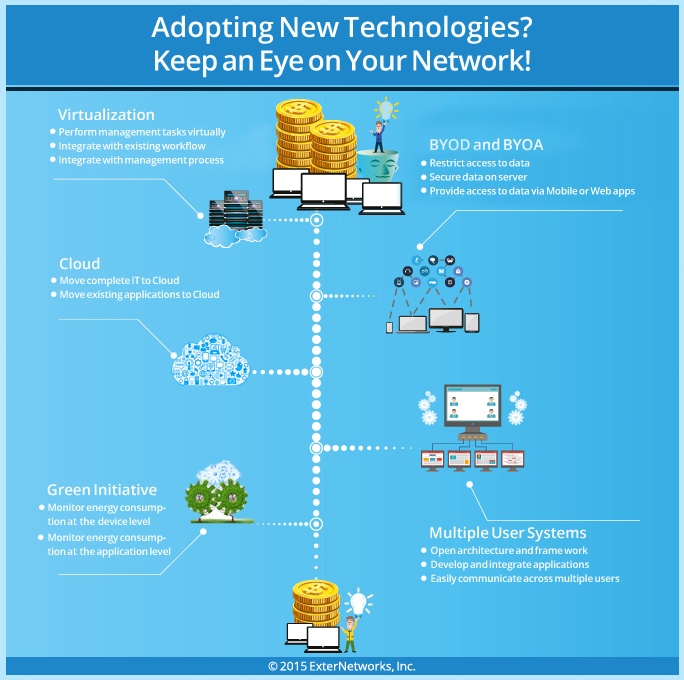
Adopting New Technologies? Keep an Eye on Your Network with Managed NOC
Every organization aims at capturing and gaining access to new markets, products and customers. However, a greater challenge than capturing new markets is that of sustaining value over the long-term....
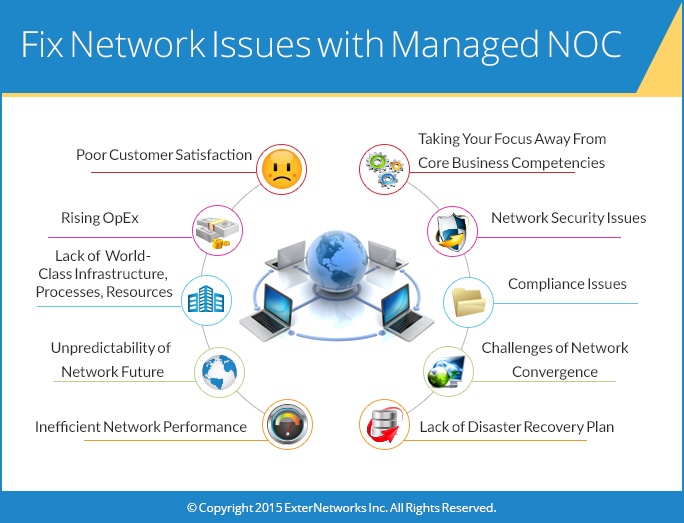
Fix Network Issues with Managed NOC
Every IT organization today needs infrastructure that can support expansion into new markets, customers, employees, vendors, and partners for business innovation and efficiency. Very few businesses succeed in accomplishing such...
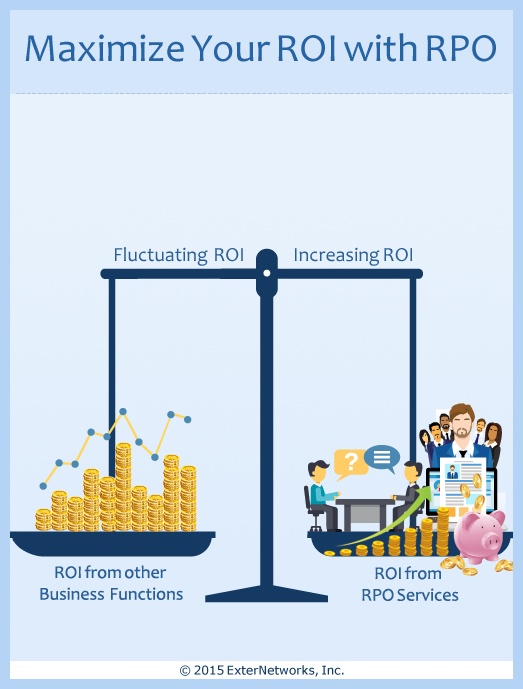
Maximize Your ROI with Recruitment Process Outsourcing (Part 1) | ExterNetworks
Recruitment Process Outsourcing (RPO) is not only a smart way of reducing your costs and maximizing your revenues and profits, but also one of the best ways to get the...
4 Changes to Your IT Policy Critical for SaaS Cloud Adoption | ExterNetworks
Migrating to the cloud opens up a gamut of benefits, but the transition can be a tad challenging. To ensure the transition is both smooth and successful, you need to...
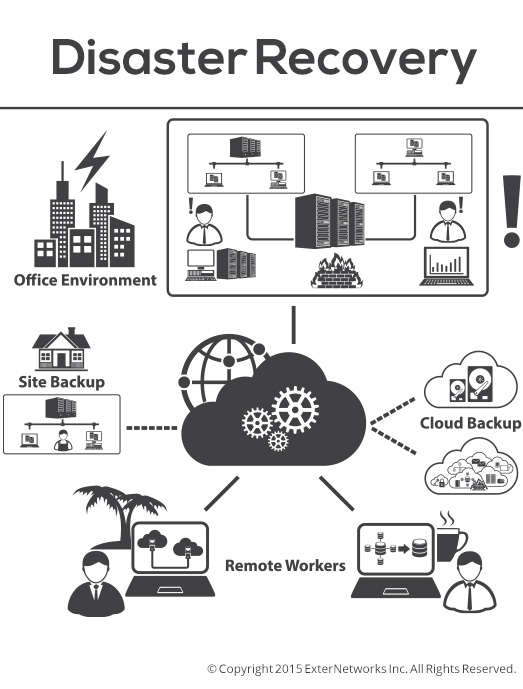
What is Your IT Disaster Recovery (DR) Plan? How Frequently Do You Perform DR Drill Tests?
Without a Disaster Recovery (DR) plan, your organization is at exceptional risk of loss of business, hacking, cyber-attacks, loss of confidential data, and more. Your DR plan can prolong your...
Is Internet of Things (IoT) Going to Be Another ‘Shadow IT’ Issue for Your Business?
As a network manager, you undoubtedly know the ins and outs of today's best network safety practices. From the creation of disaster recovery plans to approving network configuration changes, you...
4 Things You Should Know When Switching Your IT Service Providers
When businesses carry out some or all of their functions via online networks, it is imperative that a reputable Internet Service Provider (ISP) be chosen. Common problems that arise when...
Internet of Things (IoT) – The Next ‘BIG’ Investment Destination
With the IoT emerging as the next big destination for investment, many industry giants are scrambling and fiercely competing to grab their share of the revenues in the IoT market....
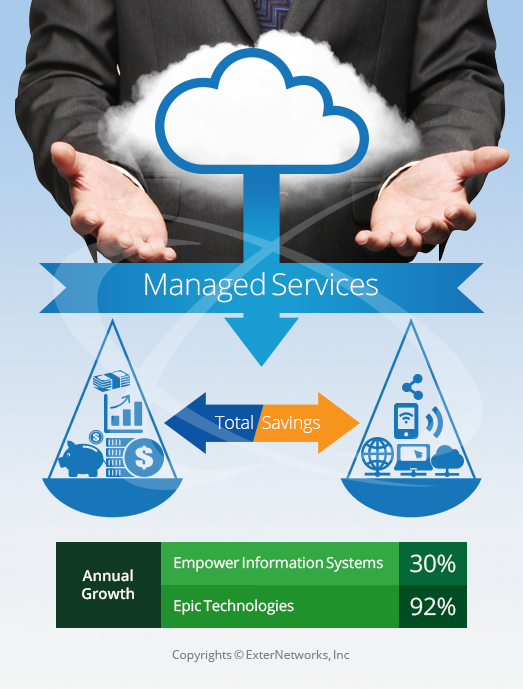
Can Managed Services Reduce Total IT Cost?
Managed IT Services play an important role in reducing IT costs, IT risks and IT issues, resulting in better customer relationships and higher profits. Managed Services Minimizing IT Cost and...
IoT & WEARABLE TECHNOLOGIES – THE FUTURE
How They Will Reshape the Enterprise IT Landscape With the recent launch of Apple Watch and more wearable technologies to follow, more and more connected devices are expected to get...
Public Cloud and NOC Service Integration
Network Operations Center Managed Public Cloud and NOC Services Integration A managed public cloud provider must pay careful attention to security in the cloud, isolation and processes while offering significant...
How the Apple Watch and other connected devices will impact enterprise IT infrastructure
This week’s Apple event highlighted the new Apple Watch, which truly embodies the advancements and innovation of technology in the 21st century. In typical Apple fashion, the features, capabilities and ability...
Make Hay While The Sun Shines – With The New Apple Watch
Today, wearable technology has contributed to a $700 million industry just in the form of wearable fitness and health technology trackers and is still growing exponentially. Of these smart wearables,...
Cyber Gang Robbed 100 Banks Worldwide – Did They Even Breach The US Banks?
Hackers have always targeted customer bank accounts but now, a cyber-gang known as, Carbanak, is stealing directly from banks, totalling over a billion dollars so far. How hackers have breached...
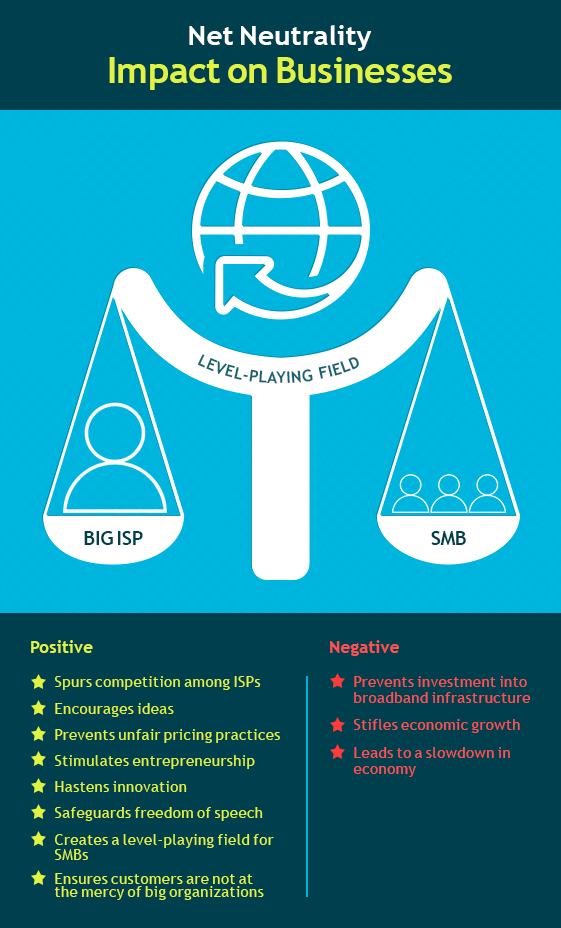
Impact Of Net Neutrality On SMBs & Other Businesses – Positive Or Negative?
With FCC ruling in favor of net neutrality, what could its impact be on businesses, especially SMBs, which rely on ISPs for delivery of its video and content. Read on…...
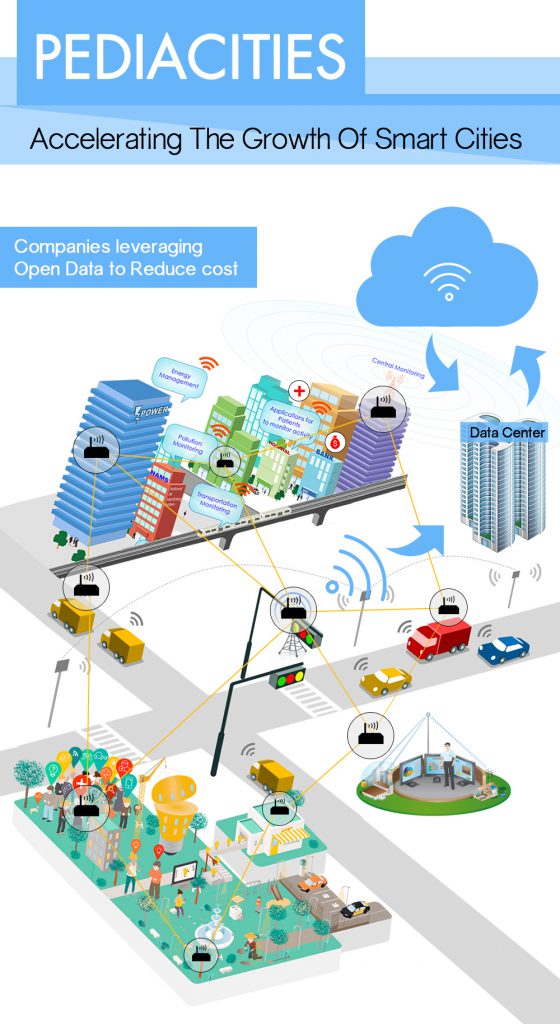
PediaCities – Transforming Communities to Create Smart Cities
In our earlier blog post, “Empowering Smart Cities with Open Data by PediaCities” we have discussed at length about what Ontodia’s PediaCities can do with raw and unstructured data, thereby creating...