Is Internet of Things (IoT) Going to Be Another ‘Shadow IT’ Issue for Your Business?
As a network manager, you undoubtedly know the ins and outs of today’s best network safety practices. From the creation of disaster recovery plans to approving network configuration changes, you understand how complex it is to keep a network safe from vulnerabilities. The truth is, as time passes, things are only going to get even more intricate due to the Internet of Things (IoT), which is growing at an astonishing rate. The IoT stands for the Internet of Things – connecting all devices on a network via a wired or wireless connection. It is predicted that by the year 2020, more than 50 billion devices will be connected to the Internet.
Don’t let IoT overwhelm your business
As the IoT continues to expand, you need to be asking yourself if shadow IT – building/using IT systems and solutions without proper organizational approval — and the IoT are that different from one another. After all, both involve the use of multiple devices on networks that may or may not be secure. Here’s an in-depth look at shadow IT and the IoT and how each of them will affect your business processes.
What is shadow IT?
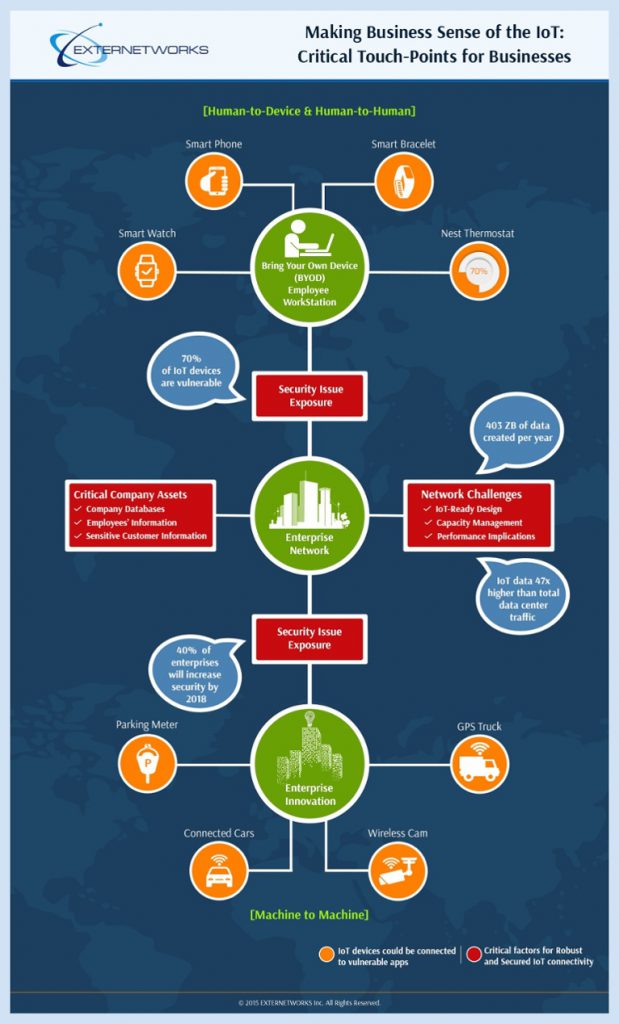
When software or hardware is being used within your company that you are not aware of, this is known as shadow IT. The term also applies to software and hardware being used that you have not approved. All enterprises need to have a strict “bring your own device” (BYOD) policy to minimize security risks. Interestingly enough, though, 72 percent of businesses who have BYOD rules say their employees are using software or hardware that is not sanctioned by their IT departments. Why even create the rules if they aren’t going to be enforced?
Years ago, most shadow IT issues arose due to employees who were anxious to access company data but failed to go through corporate channels to acquire approved hardware and software. Nowadays, however, shadow IT is massive because employees are bringing their own devices to work and using them to access large amounts of company data. And while this is perfectly OK, if the devices have been approved, many workers fail to have their devices assessed.
What is the IoT?
The IoT has expanded the way we carry out our day-to-day processes. From connecting our alarm clocks to the Internet to WiFi-connected vehicles, IoT devices are all around us. For business purposes, IoT enhances information transmission and boosts productivity. Accessing critical data via your smartphone on the subway home from work becomes a cinch, and carrying out video conferences via smart TVs simplifies long-distance communication issues.

We have entered into an era in which almost all new devices being sold in stores come with the ability to be connected to the Internet. This means that these devices can communicate with one another. Take for instance that you set your oven to come on at 5:00 pm so you can cook dinner when you get home from work. However, at 4:30, you realize you won’t be getting off until 6. You can enter this info into a compatible app on your phone, which then sends it to your Wi-Fi connected oven to tell it not to turn itself on until 6.
On the downside, the IoT augments shadow IT issues. With so many devices being connected to the Internet, it’s difficult for enterprises to keep their data secure. Take, for instance, an employee who uses an IoT device —smartphone — that has not been approved by your IT department to access corporate data. What happens if this device gets lost or falls into the wrong hands? Because your IT department didn’t approve its use, it most likely doesn’t have a mobile data management solution installed, meaning any corporate data accessed on it is not secure.
What complications do each of them bring to a business?
When the entirety of your enterprise is based mainly on IoT devices, this could present a roadblock to productivity. IoT devices require a connection to the Internet to communicate with one another. When connectivity is lost, information cannot be sent or received.
As expected, shadow IT is, in itself, a major complication too. When rogue deployments take place, enterprise data is greatly compromised, because the programs and devices aren’t subject to corporate compliance-related protections like approved devices are.
With the IoT and shadow IT, bandwidth and power efficiency conundrums will increase, too. As more devices become connected to your network, you’ll need more and more power and bandwidth to support their data usage. Take for example that you currently have only 20 devices operating on your company’s bandwidth. With the IoT, there will likely come a time when this number doubles, if not triples. The data that these devices use will take up a large amount of bandwidth, possible so much that you’ll need more bandwidth to accommodate the device’s bandwidth needs.
How to overcome these complications?
Connectivity issues can be resolved by ensuring your workers have round-the-clock access to the Internet. This means they will need access at the office, at home and on the go. Fortunately, there are many portable Internet service providers. And there’s a high likelihood that if your workers have a smartphone, they will have mobile data that can be used to power their IoT devices.
As far as resolving shadow IT issues, your IT department needs to conduct regular reviews of its network data— identifying where data is coming from and where it’s going to. If any non-compliant hardware or software applications are being used, the issue needs to be remedied as quickly as possible.
All network managers should be required to turn in daily reports to your CIO to ensure that IoT- and shadow IT-related obstacles are identified and addressed in a timely fashion. When it comes to handling these agendas, time really is of the essence, because any type of vulnerability could lead to a data disaster.
To address power issues, you will need to monitor energy usage to see where reductions can be made —perhaps some of your workers are using business-only laptops for personal use when they could be using their own tablets, smartphones or PCs. After all, one of the primary goals of the IoT is to reduce power consumption and conserve energy in an effective and efficient manner.
To appropriately meet bandwidth requirements, you’ll want to take advantage of 4G networks to power your IoT devices, and when 5G networks become available, that’s definitely a bandwagon you’ll want to hop on.
The Takeaway
Shadow IT and the IoT are quite similar, and they both bring their own challenges to the information technology table. However, with effective and secure practices, such as regular device monitoring, shadow IT and the IoT can be used to enhance your overall operational efforts. Years ago, we chose for ourselves which objects we wanted to connect to the Internet — computers and smartphones — but nowadays, everything is being connected by default — watches, appliances, TVs, etc. We can thank shadow IT and the IoT for this new digital area.
ExterNetworks’ Value Proposition
As the IoT moves into the mainstream of business with the explosion of wearable and smart devices, you will have to successfully overcome the challenges related to managing humongous amounts of data generated by your enterprise, while simultaneously ensuring security of your organizational infrastructure and network. Managed Services Providers (MSPs), such as ExterNetworks, can help businesses harness IoT technologies to the hilt by creating new business models.
At ExterNetworks, business transformation is at the core of our services strategy. We can help you innovate to generate revenue or gain productivity and cost efficiencies starting with one of these solutions: