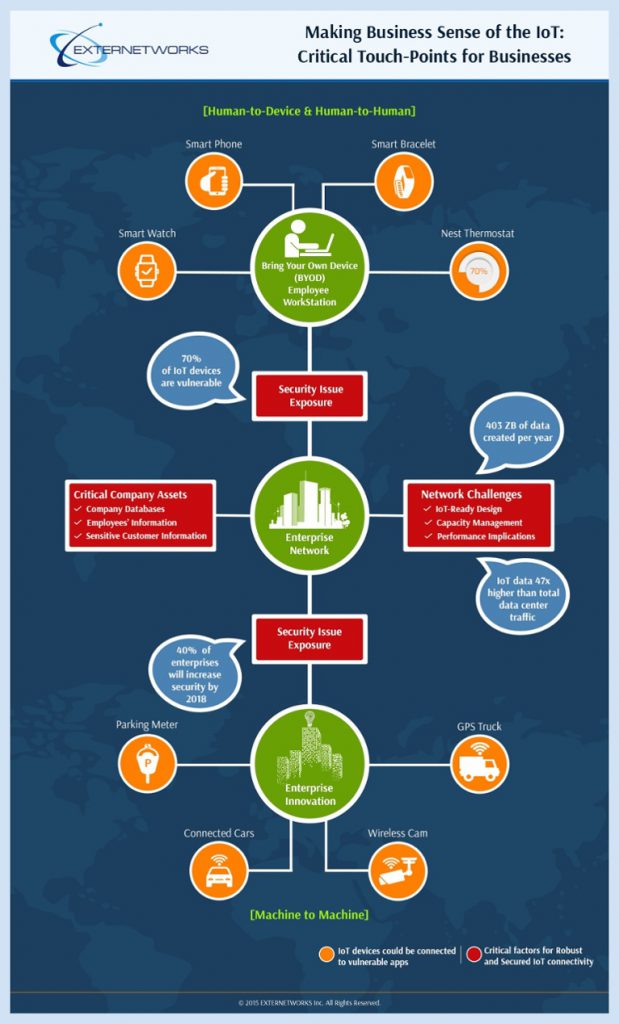
Recent Posts
Mitigating Top Mobile Security Issues to Shield Your Privacy, Data,...
Today’s world has marked the dawn of an era where everyone is ‘always connected’ through mobile devices. With businesses increasingly allowing their employees to carry out work-related tasks on their...
8 Reasons to be Smart About Your Web App Development
Custom and Cross Platform Web App Development is growing at an exponential rate. The demand for creating customer-centric applications is outpacing the ability to meet the supply, since more developers...
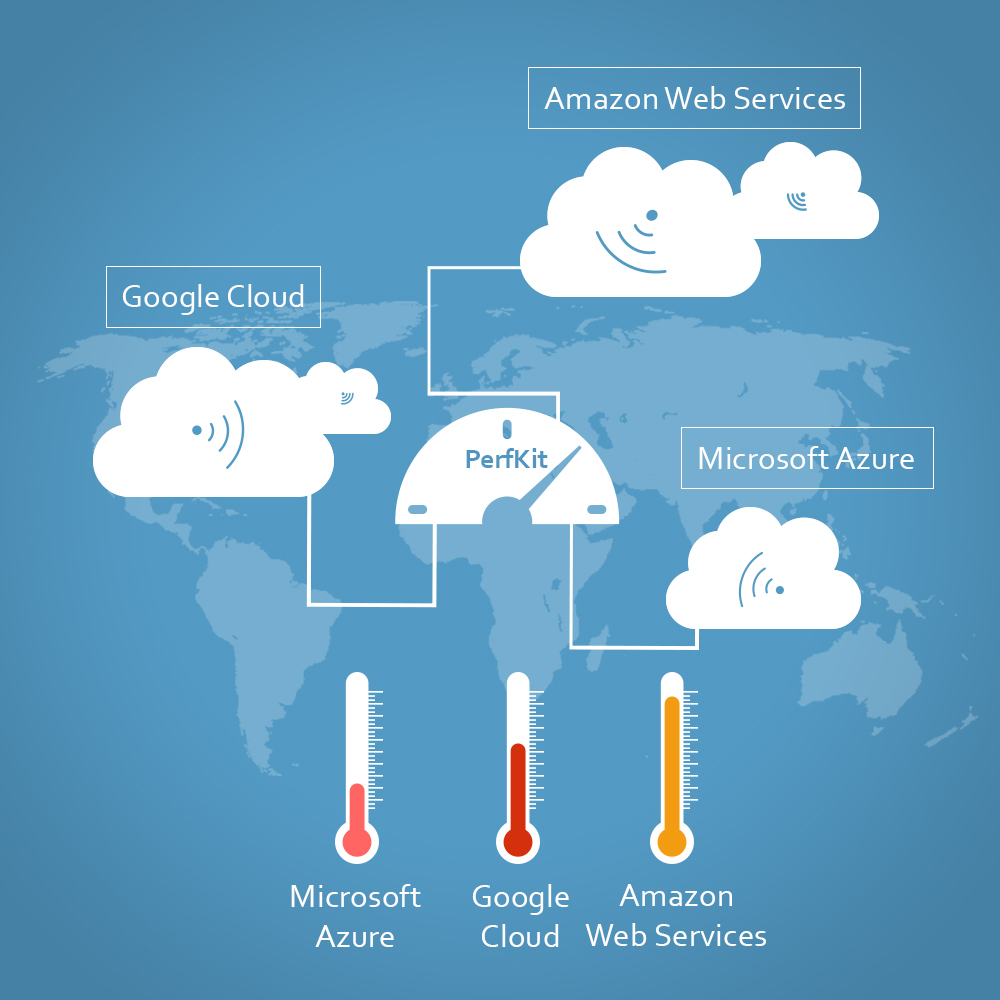
Google Perfkit Sets ‘Benchmark’ For Cloud Applications. WHAT’S NEXT?
Google Perfkit eases developers to evaluate performances of Google, AWS and Microsoft Azure cloud computing services, and determines the best cloud platform for your app. Many companies and application providers...
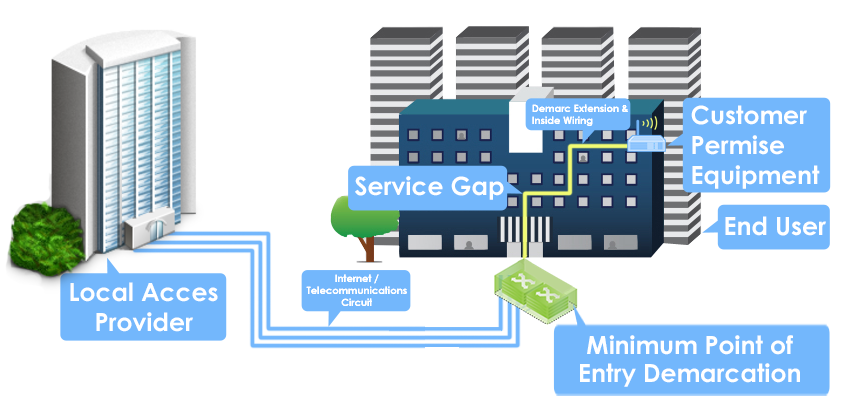
Benefits Of Managed Services To Avoid Delays In Bandwidth
What you need to know about Site Readiness to accelerate the deployment of your technology systems. How Managed Services Can Avoid Delays In Bandwidth The deregulation of the telecommunications industry...
Cloud vs. Managed Cloud – The Questions You Must Always...
Ready to migrate to cloud? Reap the benefits of cloud adoption by driving innovation through Managed Cloud Services. Today, Enterprises of all sizes are using Cloud Computing in one form...
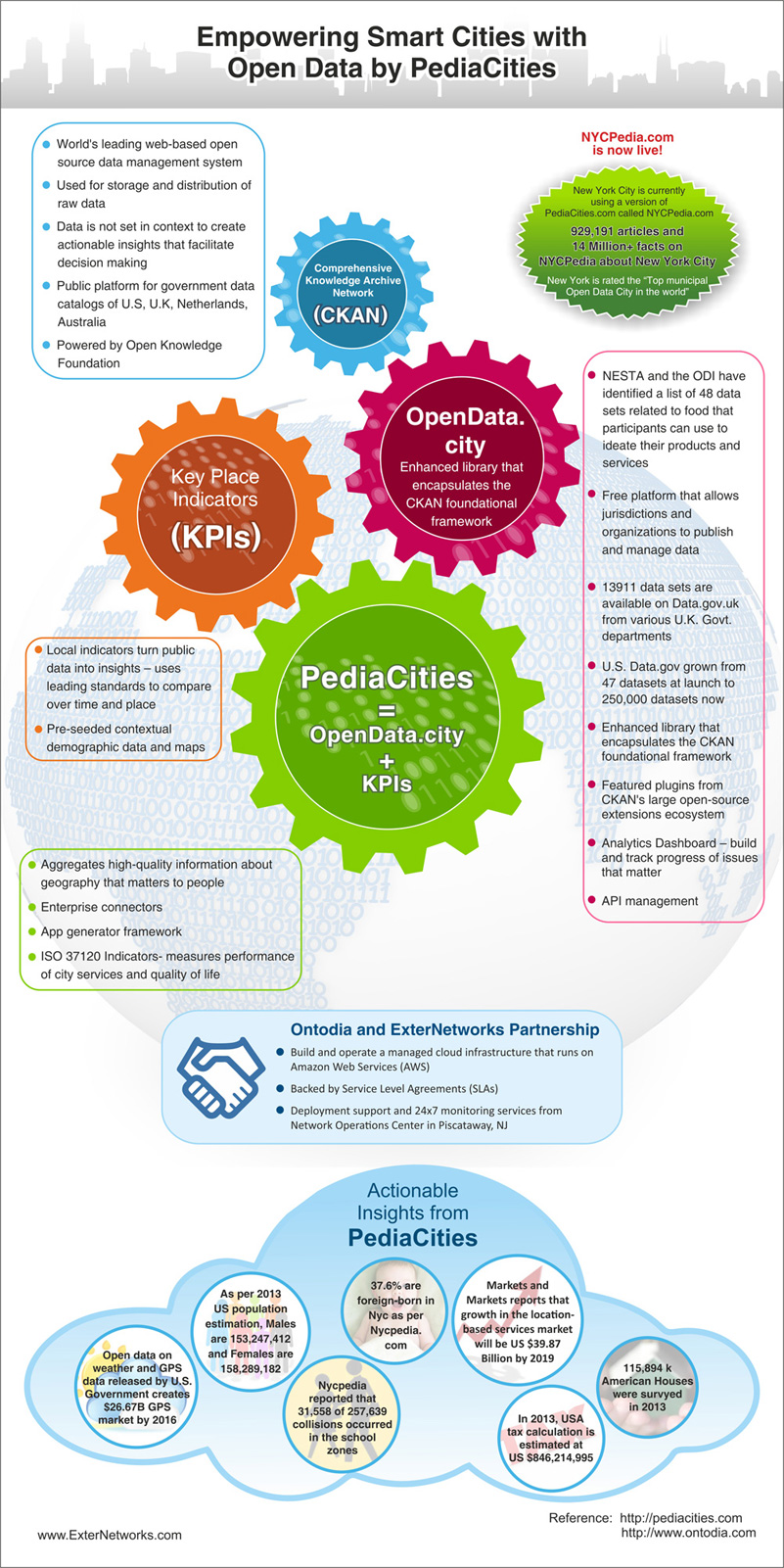
Empowering Smart Cities with Open Data by PediaCities
In this era of social media we have access to raw data like never before. Our ideas, likes and dislikes, and the Internet of things (IOT) are captured by social...
How To Get 24X7 Support And Increased Output By Outsourcing
Years ago, businesses had to build their own software applications according to the tasks that they needed to carry out. However, thanks to SaaS, they can now easily adopt outsourced...
Which Is The ‘Right’ Recruitment Agency For You?
As a job-seeker, one is always in a quandary as to which is an effective staffing agency and which is not! With an influx of too many ineffective staffing agencies...
Identifying The ‘Right Recruiting Company’ To Maximize Your Talent Investment
The US temp staffing industry is booming, with its size expected to increase to 3.4 million employees in 2020, with $185 billion in temp revenues and 2.2% temp help penetration....
The Case For Detaching Recruitment From HR & Retention Management
In today’s challenging business environment, managing your company’s human capital is critical to its success. Detaching ‘recruitment’ from ‘HR and retention management’ is one of the essential steps. Is your...
Benefits Of Managed Services To Avoid Delays In Bandwidth
What you need to know about Site Readiness to accelerate the deployment of your technology systems. How Managed Services Can Avoid Delays In Bandwidth The deregulation of the telecommunications industry...
Cloud vs. Managed Cloud – The Questions You Must Always...
Ready to migrate to cloud? Reap the benefits of cloud adoption by driving innovation through Managed Cloud Services. Today, Enterprises of all sizes are using Cloud Computing in one form...
Exploring Vulnerabilities in Network Security
Do You Understand the Challenges of Network Security? In 2016, Gartner estimated that 99 percent of network security attacks were due to vulnerabilities technical professionals had identified at least one...
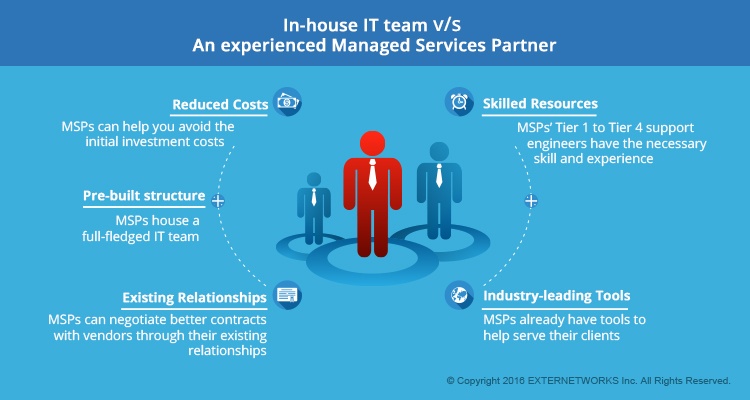
Top 5 Reasons Why SMBs Must Rethink of Hiring an...
It’s so tempting for SMBs to want to hire an in-house IT team to manage their network infrastructure. After all, if you’re outsourcing to an MSP, you won't have someone...
Balancing Risk and Rewards – Panel Discussion
SmartCEO and Anchin, Block & Anchin LLP gathered a panel of Future 50 Awards alumni to discuss how they deal with the dizzying demands of growth. ExterNetworks was awarded the...
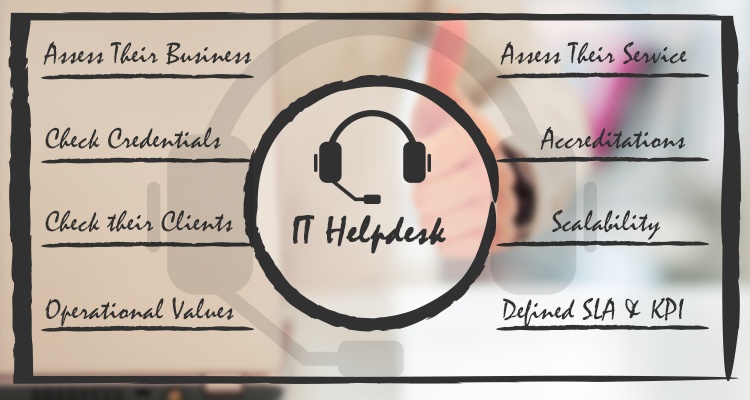
Critical Questions to Ask Your Potential IT Helpdesk Partner
When your company’s needs have outgrown your in-house IT support team’s resources, outsourcing to a reliable helpdesk partner could be a strong solution. Outsourcing can bring tangible and intangible benefits...
Can CEOs Now Have The Best Of Both The Worlds?
The job of a CEO has never been more challenging. This position can sometimes be lonely and isolated. It can be a wrathful position with issues for which the slightest...
Benefits Of Managed Services To Avoid Delays In Bandwidth
What you need to know about Site Readiness to accelerate the deployment of your technology systems. How Managed Services Can Avoid Delays In Bandwidth The deregulation of the telecommunications industry...