IoT: How Secure are You With the Internet of Things? Externetworks
Increasing network security breaches and cyber-attacks make proactive and regular security audits a critical priority for CIOs, Information Security Officers, and Network Managers. As the Cloud and the Internet-of-Things (IoT) make it hard to track devices that connect to enterprise networks and when data interaction is done in a more open fashion, your business’ vulnerability increases exponentially. So make it your priority to get a technology and information systems audit by a certified CISA auditor, who can provide a structured audit/assessment and framework for hardened security monitoring and IT systems control.

Checklist on how to ensure network security with the help of CISA audit
A traditional enterprise network usually faces common challenges such as spyware, malware, and professional hackers who want to infiltrate networks and steal information. Combine these hurdles with Internet of Things (IoT) devices, smartphones, tablets, TVs, cars, etc., all of which are now beginning to interact with the company-issued laptops that are connected to the network. With all of the threats that are ongoing in the word today, it becomes clear that your enterprise might not be as secure as it should be. Security weaknesses are sure to be endured if you don’t create an effective IoT security plan. Here’s a look at the steps you can take to make your company as secure as possible.
You must frequently monitor your connected devices
Hewlett-Packard released a statement stating that 70 percent of IoT devices contain serious vulnerabilities. This goes to show that a portion of the IoT devices connecting to your enterprise’s IT systems are likely to be susceptible to hackers. Identifying such vulnerabilities can only take place if you look for them; and to do this, you must frequently monitor your connected devices. Frequent monitoring must also include devices that are used as part of a “bring your own device” (BYOD) plan.
All devices need a two-factor authentication process — password and PIN protection. You should check each device regularly to ensure that its operations are encrypted and, more importantly, you must check for counterfeit chips or embedded codes. It’s also imperative to check your network connection on a daily basis and make sure it is operating as an intranet, meaning it’s not open to the public.
You will need to initiate processes that continually monitor the traffic flowing in and out of your network on IoT devices. If a security issue arises, it is imperative that you track it and shut it down immediately, logging the information to investigate how the intrusion took place and how to prevent it from happening again.
Periodical Audit of Existing IS Policies and Procedures (CISA Audit)
Every network device (Switches, Routers, Firewalls, IDS, and Servers) must be audited yearly which should ideally include an Internal as well as an External audit. This will assist in finding gaps in your network and allow you to take risk-mitigating measures to deploy fixes for vulnerabilities that are identified. Scanning of network devices on a weekly scheduled basis is highly recommended.
Information Security Officers Need to Turn in Daily Reports
Network managers and information security officers must be held accountable for their day-to-day responsibilities, and the most efficient method of holding information security officers accountable is by requiring them to turn in daily reports. These reports should provide in-depth information about any security vulnerabilities that were identified and addressed during the day.
The report should also outline any software or hardware updates that were implemented, and the reasons behind them. New IoT devices should be documented, and confirmation that they were assessed for security and compatibility functions should be noted. The report can also discuss any new strategic planning that is taking place to enhance IoT practices. Lastly, the report should cover any recruiting, hiring and training information relating to new IT staff.
Only Secure Devices Should be Able to Connect to Enterprise Networks
As stated before, IoT devices must be regularly monitored to ensure they are secure. Your company should have a strict policy on what devices can and cannot be connected to your enterprise network. All devices should have password and PIN protection, and a mobile device management solution should be installed on each one, as well.
Mobile device management software will enable you to collect real-time information about the data being used on the devices. It also allows you to see that all necessary security updates have been implemented on each device. Any noncompliance issues that are identified should be included within the daily report turned in by the information security officer.
It’s also imperative that these devices each have an app downloaded that serves as a location and disaster feature. If a device were to be lost or stolen, the app could be accessed via a computer to determine the device’s location. The app could also be used to wipe the device clean if it cannot be found and must ensure that corporate data won’t be compromised.
All employees should be trained in how to work with IoT devices. Employees should be taught how to identify malware and spyware, and learn what best practices should be used to avoid downloading it. Safe browsing and application download tips and tricks should be part of this training.
Our CEO, Malik Zakaria, said that cyber security is a primary concern in the advancement of IoT, and it is crucial for organizations to take numerous preventions to secure critical assets from cyber-attacks.
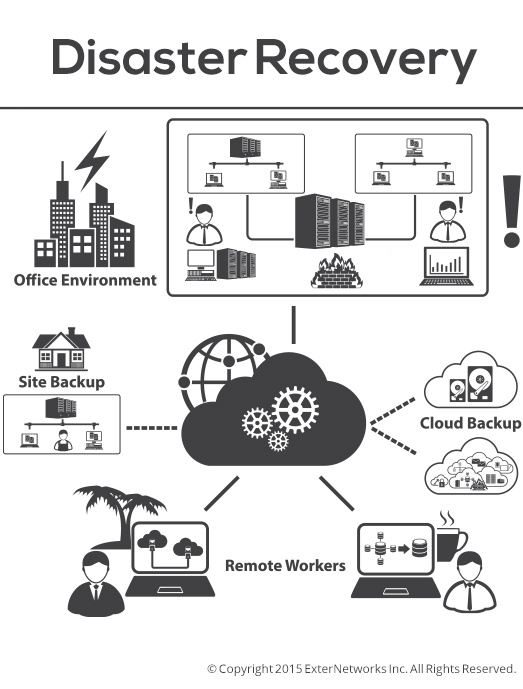
Create and Maintain a Disaster Recovery Plan
To be secure with the IoT means you must create, implement and regularly monitor a disaster recovery plan. It should outline your backup strategy as well as include daily backups of all data on all essential services. You will want to steer clear of differential backups, so if a disaster were to occur, you would not have to sort through several backups to complete the data restoration process.
Your disaster recovery plan should have a list of all IoT devices that are connected to your network, as well as the applications and software programs that are downloaded. If your company provides business-critical services to a particular group of customers, you should have a list of these customers with their contact information, address, phone number and email address. If your network were to go down, you would need to notify these customers, and provide them with an estimate of when the network restoration process would be complete.
Diagrams of all networks should be a part of your disaster recovery plan. It should be a visual representation of network connections, and will need to cover the following details:
- IP addresses
- Model
- Serial numbers of equipment
- WAN default gateway
- Local IP subnet
- VPN policies
- Firewall configurations
- DLCI information
- Circuit numbers
- WAN carrier contacts information
Your plan should also have a synopsis of your disaster recovery teams, safety and security team, technology team, damage assessment team, etc. These teams would work together during a disaster to complete data and network restoration processes as quickly as possible. A robust disaster recovery plan can come as part of an overall managed services package that provides full perimeter monitoring, management, and support for your infrastructure. This is where a managed service provider like ExterNetworks can assist enterprises.
The Takeaway
No enterprise is entirely safe from the vulnerabilities that the Internet of Things brings forth. However, when your organization learns all that it can about the IoT and takes appropriate measures to protect itself from security issues, the IoT can then be used to enhance productivity and increase profit levels. To ensure this happens, you should have at least one Information Security Officer or a Network Manager, who can focus mostly on IoT-related issues. In general, it is always good to consult with organizations (or MSPs) that focus their time looking at the reliable and secure operation of technology. ExterNetworks can help you throughout your information technology lifecycle – from the initial network design and optimization to ongoing Managed Services for monitoring and management of your IT infrastructure and applications. Click here to learn more about our full portfolio of services. Contact us for a free security consulting or with any question you may have. You can also connect with us via social channels – Twitter, Facebook, or LinkedIn.