Surviving the biggest threat of the year – Ransomware
Only when you thought you did nothing more than clicking on a web link, your files are encrypted and locked, and you can’t access your data. This is a painful case of “holding your data hostage”, and you are asked to pay ransom to get your files back. Cyber attackers work incessantly to find workarounds to infiltrate your security systems. These attacks are only getting sophisticated over time.
Over the past three years, Ransomware attacks have increased steadily. Towards the end of 2015, Ransomware stood out as the most destructive malware of year.
In the most recent ransomware attack that happened in Plainfield, NJ (Source: CBS news) hackers have held hostage the data from municipalities. Officials have reported that they lost access to 10 years of data and that 3 of their servers have been compromised.
Ransoms can escalate to business crippling amounts of dollars, imagine what the loss of large volumes of data can do to your business, operationally and financially.
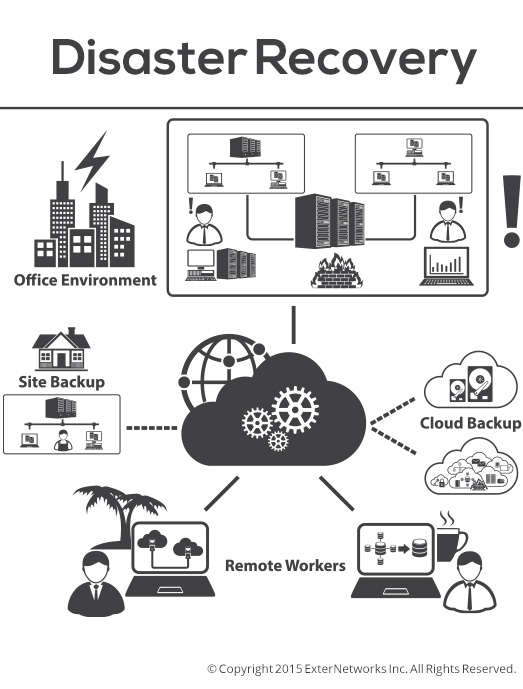
It is in every organization’s best interest to take a pulse of its current IT infrastructure and ensure it has the right security mechanism in place. We know the ins and outs of securing the IT infrastructure and would like to share these insights to help you prevent security disasters.
Related Blog Posts: