Optimize Your Enterprise Network to be BYOD and IoT-Ready
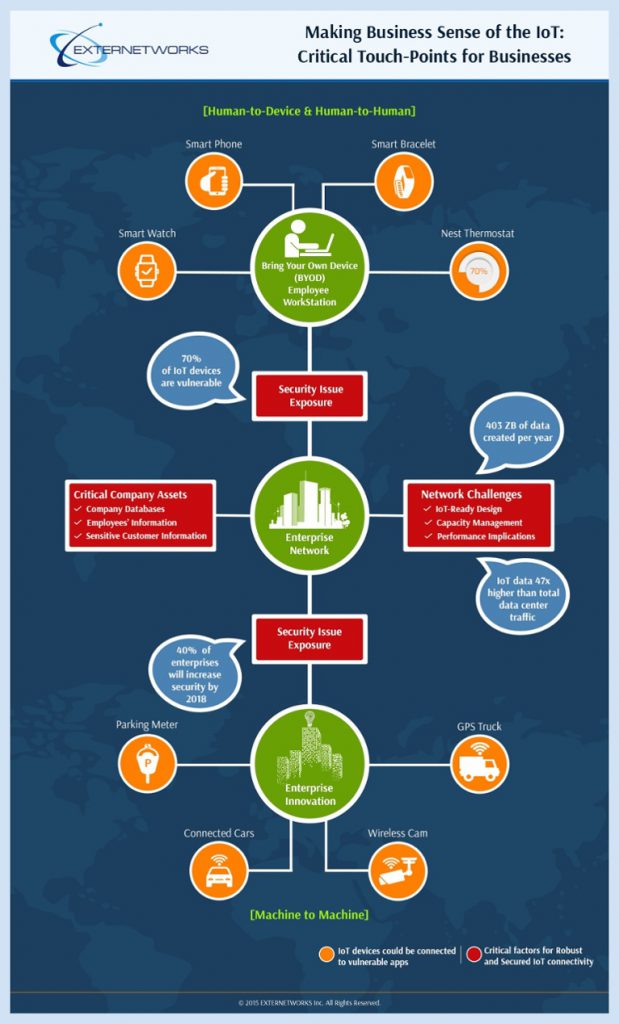
With the advent of the Internet of Things (IoT) and ‘Bring Your Own Device’ (BYOD) culture, your enterprise network is sure to face a different set of challenges and roadblocks that it had never faced before. Owing to IoT and BYOD, people have connected their mobile devices such as tablets and smartphones as well as other IoT connected assets to your enterprise network. So, it is but natural that the number of devices connected to your network environment is much higher today than it was a few years ago.
However, the volume of connected devices is not the only impact that BYOD and IoT will have on the enterprise network environment. Another major worry with BYOD and IoT in your network environment is their combined impact on network security and network capacity planning. In this blog, we will see how BYOD and IoT impact the enterprise network as more and more users bring their iOS and Android devices into the enterprise network, which places unprecedented demands on companies’ WLANs and network infrastructure.
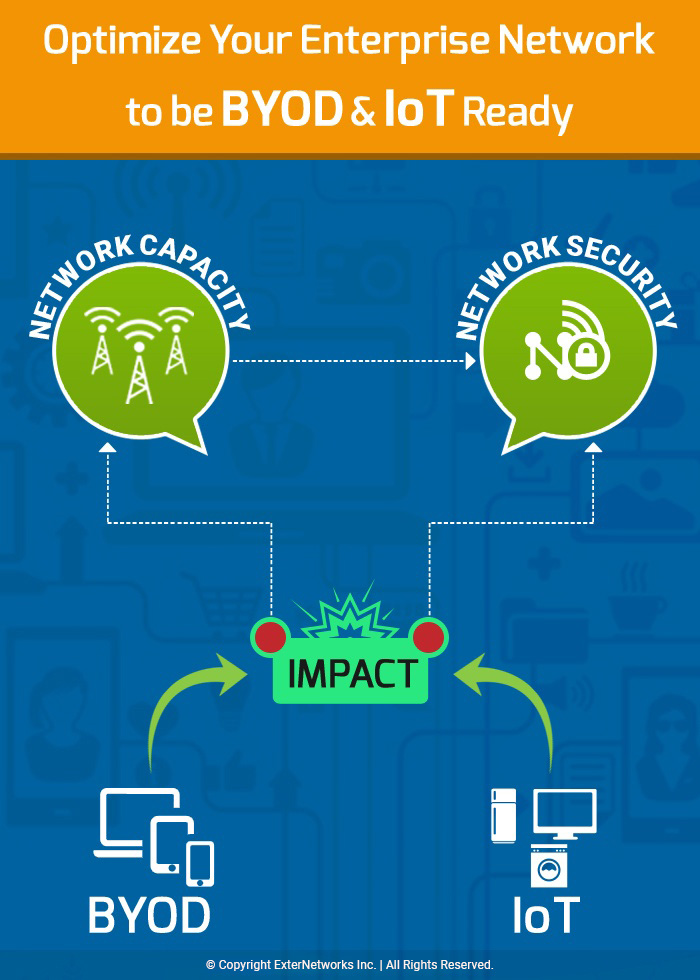
BYOD and IoT impact your enterprise network in more challenging ways than you know.
Today’s business world is all about globalization and mobility. It is no wonder that with many businesses operating globally, employees need a higher level of mobility and flexibility to fulfill their job functions anywhere, anytime. This has led to more and more enterprises constantly striving to offer higher mobility to their employees, with an aim to increase employee efficiency, productivity, and flexibility. This has given rise to the use of BYOD and IoT, where employees bring their own devices to work and various assets are connected through the IoT. More and more employees are accessing your enterprise network from within the company network, but also beyond the firewall with tablets, smartphones, laptops, and home PCs.
This ubiquitous connection of devices over the network has placed greater emphasis on the IT executives, who tackle daunting challenges and pressures in maintaining the network. The IT executives have to constantly be on their toes to adapt to different ways in which they manage, enable, and secure end-user access to enterprise resources, based on the devices they are using. Today’s network administrator has to take care of the network and also worry about securely connecting and monitoring both corporate-owned and personal devices.
Thus, businesses today have to think seriously about the advantages that BYOD and IoT render to their organizations, and at the same time bear in mind the impact that BYOD and IoT will have on their enterprise networks. Both BYOD and IoT will help an organization to offer its employees a platform for ongoing, collaborative and productive tools. However, it is imperative that once these devices get connected to your enterprise network, you understand their impact and strike the right balance between the advantages they offer and the challenges that they pose to your network. Hence, the real challenge for IT is not only getting devices onto the network but also about what to do with them once they’re connected to your network. Let’s understand the impact that these connected devices can have on your enterprise network.
What is BYOD?
How many times have you accessed your official documents on your personal tablets, smartphones or laptops? Many times you may have checked your email by accessing your company’s network on your own personal device such as your smartphone. In today’s fast-paced world, employees as well as organizations are more focused on getting the job done. This has paved the way to the proliferation of smartphones and tablets into computing devices. Today’s devices are equipped with faster components and better integration that lend efficient support to help such devices in connecting to enterprise systems and networks. So, many times an employee may carry out his regular job functions through multiple devices. These multiple devices, such as a smartphone, tablet and so on, may be purchased by the employee himself or may be provided by his employer. Nevertheless, these multiple devices are then used by the employee for both personal as well as business work.
This habitual practice of using smartphones and tablets for both personal and business use has given rise to the concept of ‘Bring Your Own Device’ or ‘BYOD’. BYOD entails the use of multiple devices that are brought to the workplace and then used to do personal as well as official tasks. The practice of BYOD has spread widely owing to the simplicity, efficiency and mobility that our today’s smartphones and tablets offer. Hence, more and more employees are using BYOD and fulfilling their job functions with greater ease that is offered to them by simple-to-use mobile applications. You can work using BYOD from almost anywhere, anytime, and share files without going through the hassles of copying them on to a pen drive or emailing them.
Initially, at the start of the BYOD, it was primarily being used by employees, business partners, and users to connect to the corporate network and perform some generic tasks such as accessing the corporate e-mail, calendar, contacts, etc. However, BYOD has grown to encompass much larger functions, as more and more people started using their personal devices for official work by connecting them to the enterprise network and accessing enterprise resources and applications. It is natural that with such large numbers of devices connecting to the enterprise network, Mobile Device Management (MDM) and functions associated with MDM are becoming increasingly important. Organizations are now faced with various concerns such as ensuring locking of a device and erasing of its data remotely in case it gets lost or stolen, or when an employee is terminated. Therefore, it is imperative that an organization’s BYOD strategy should propel it towards purposeful infrastructure, security, and wireless innovation and provide a solid reason for BYOD investments.
What is Internet of Things (IoT)?
IoT is an enabler of the Internet of Everything (IoE) ecosystem, comprising people in addition to process, data, and things. This ‘people’ component of IoE, by and large, drives a form of collaboration-based solutions, whereas, the IoT-driven solution, do not comprise people, but instead comprise data, process, and things.
Thus, IoT links remote assets and provides a data flow between the asset and centralized management systems. The IoT incorporates networks of physical objects and connected sensors that are controlled and operated automatically. These sensors automatically gather information about physical assets such as devices, machines, facilities, equipment, vehicles and so on to monitor their condition or behavior. So, the assets can then help furnish real-time information on condition, location, functionality, and so on. This information is then used to understand the asset’s current condition and control it to improve decision-making, and optimize processes and use of the resource.
Impact of BYOD and IoT on Enterprise Network
An organization may find certain compelling reasons to take up BYOD and IoT. However, the enterprise BYOD and IoT management can be a daunting task in itself. One of the primary hassles that an enterprise’s network faces while adapting to BYOD and IoT is that it makes managing bandwidth and content harder. The IT department of the organization will be caught up in various daunting challenges such as integrating the employee-owned devices into existing network, policy, and regulatory frameworks. As the number of devices, bandwidth, and applications demand grows, it becomes more challenging to manage the growth of mobile devices and traffic.
Most organizations feel that implementing an efficient Mobile Device Management (MDM) will solve the problems of BYOD and IoT, and enable employees’ devices to connect to the enterprise network without compromising corporate data and infrastructure. However, today’s BYOD and IoT market has moved beyond MDM, as Mobile Application Management (MAM) and Mobile Information/Content Management (MI/CM) have become decisive for user collaboration and productivity.
Thus, before choosing BYOD and IoT for your organization, you should bear in mind that your enterprise BYOD and IoT might not even save you money in the long run if you take into account the BYOD and IoT management, and infrastructure costs. Your organization may still end up paying some of the bills for your employees depending on your cost-sharing policies. So, even after adopting BYOD and IoT, your company may still be paying the bills for data plans, devices, telecom expense management systems or man-hours to keep track of it all.
BYOD and IoT Challenges
The key challenges that BYOD and IoT face are:
- One of the biggest challenges that an organization faces in BYOD and IoT is that of Mobile Device Management (MDM). Only an efficient MDM can enable an organization to centrally regulate, control, and manage mobile device access across its enterprise network.
- BYOD and IoT require that an organization should have a robust Wi-Fi infrastructure. This is because Wi-Fi has become the primary means of network access today, with the continued growth of BYOD, IoT and mobile devices. So, an organization needs to provide a high-quality wireless experience through a robust Wi-Fi infrastructure. Such a robust Wi-Fi will help ensure wired-like performance, ability to handle a high density of wireless clients, and managing and easy upgrade of the Wi-Fi to the latest technologies.
- Continuous support from the IT department is another challenge of BYOD and IoT. Employees may be familiar with their own devices, however, they still require continued support at different stages of BYOD and IoT at workplace. Employees may get in touch with the help desk staff for various concerns such as: to gain access to enterprise networks, or when devices break or malfunction.
- One of the biggest challenges of BYOD and IoT is security. BYOD and IoT make securing all the different devices and operating systems almost unimaginable. BYOD and IoT require an integrated security system that ensures not only the encryption of wireless traffic, but also takes care of onboarding of devices, access controls, ability to provide guest services, and user tracking.
- Apart from the security of all the connected devices and the enterprise network, the IT department has to also deal with the hassle of the complexity of managing several, multiple, unknown devices.
- A few other issues that come with BYOD and IoT and need to be addressed are: licensing, legal issues and more.
Overcoming Enterprise BYOD and IoT Management Challenges
Now, let’s take a look at some ways of overcoming enterprise BYOD and IoT challenges:
- As a ground rule, you should use ‘security’ and ‘simplicity’ as a fundamental rule while adapting your enterprise network for BYOD and IoT. Keeping these two aspects in mind, you should design and create a successful network architecture for today’s BYOD and IoT connected devices.
- You can improve your BYOD and IoT setup, and ongoing network management by using tools that integrate network, device, and policy management. Such a unified management workflow will ensure that the policy settings will effectively diffuse throughout enterprise networks and to devices.
- The other key aspects to keep in mind while dealing with BYOD and IoT are capacity and scalability. You should bear in mind that your enterprise network will be able to better adapt to changing conditions if it is capable of scaling without weakening its security capabilities or simplicity of operation.
- You can also use your organization’s Virtual Desktop Infrastructure (VDI), if you already have one, to overcome BYOD and IoT challenges through application and desktop streaming. These help to retain information in the data center to help with device security.
- You should not limit the use of the devices by your employees for business as well as personal use, if you want to ensure a successful implementation of BYOD and IoT in your organization. This is because when employees are restricted from using their devices for personal use, they would become reluctant to use the device for business purposes also. This would sabotage your entire BYOD and IoT project and also the benefits that you plan to gain from implementing the same in your organization.
- You can gain better control of your enterprise BYOD and IoT projects if you draw up a complete, exhaustive and detailed BYOD and IoT policy. This BYOD and IoT policy should also include details of how your organization plans to maintain a balance between compliance, security, and user acceptance in order to make your BYOD and IoT project successful.
- You should choose a simplified network structure as its management is easier and it allows your IT staff to gain better transparency into network and device activity. Such insights can then help carry out complex changes correctly and efficiently.
- You should implement a slow and steady change in your enterprise network that allows your network, employees and the organization, as a whole, to handle the pace of change, recognize transformational opportunities, and respond with confidence. You can do this by developing a detailed process for BYOD and IoT conception, planning, delivery, evaluation, course correction and improvement.
ExterNetworks is a single source provider for end-to-end BYOD and IoT solutions to connect and optimize your organization’s processes and systems. We seamlessly deliver BYOD and IoT solutions by providing you access to our experienced resources with specialized skills. We provide complete IoT solutions to help you gather, analyze and interpret real-time information that enables more accurate understanding of status of the connected assets. Also, we help provide you end-to-end implementation of BYOD in your organization to help increase your employees’ mobility, productivity and efficiency. We offer BYOD and IoT solutions that span a broad range of applications, technologies and enterprises.