Critical Touch Points of IoT
The Internet of Things (IoT) is fast becoming a household name, as it is the next big area of development in the global technology landscape. Businesses need to take the IoT and it’s potential very serious if they do not want to end up like Blackberry who missed the boat on Apps and the open integration of the mobile platform. However, in doing so, businesses need to address at least two key challenges that IoT will bring to their operations – (1) Security and (2) Network Capacity Impact. Whether a business does something specific or not with the advent of IoT, IoT will definitely touch its operations. Just take your employees and the daily IT users. See how they interact with your enterprise infrastructure network as shown in the illustrative diagram below, “Making Business Sense of the IoT: Critical Touch Points of Businesses,” to visualize the points at which they open your network to the IoT.
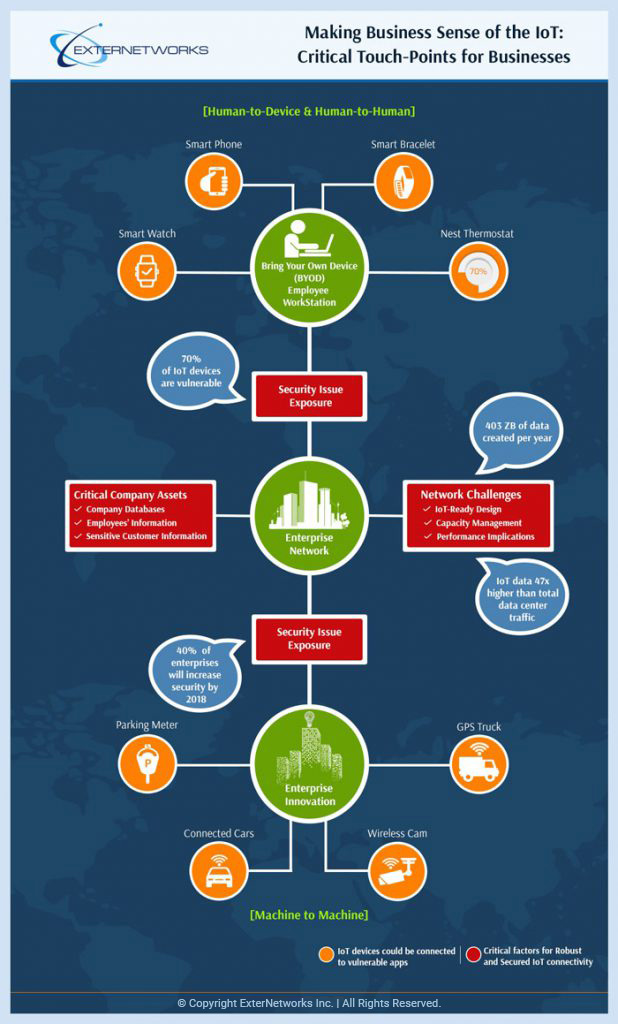
Internet of Things (IoT) will touch your network – are you prepared for the unintended consequences?
IoT & Security

Your users alone will connect many different types of devices like their smartphones, sports watch, and other wearable devices to your network; they will also install programs or access programs/app via the web to monitor their connected home thermostats, etc. Research shows, 70% of IoT devices are vulnerable to security breaches. So whether you declare an IoT strategy or not, IoT will be coming to you. This is the point of interaction of your users’ connected things and your network’s open security loopholes. It is scary as most of these new loopholes are not a part of the traditional security protection tools. Introducing a challenge that is only going to increase in magnitude with the exponential permutations of communications between the billions of connected devices.
For example, in the recent Apple iOS App Store breach, hackers were still able to launch a large-scale cyber attack in spite of stringent app review processes and high quality assurance posture of Apple. This proves that you need to keep a constant pulse on your security posture. A study by the security firm Veracode, found that gambling apps installed on mobile devices of any organization’s employees compromises their corporate data. Such free apps often gather device and user information, which is all the more critical in the case of Bring-Your-Own-Device (BYOD) programs. This makes application-blacklisting policies a must and no longer an option if your business is to avoid such vulnerabilities.
In the industrial space, similar types of loopholes open up your network to attacks. It really doesn’t matter if you decide to use connected devices in-house, build services for connected devices that you wish to sell, or have no plans to use or build IoT services; it is guaranteed that IoT will touch your network. You want to make sure that when it touches your network there are no unintended consequences to your daily operations. Just take a look at what hackers were able to do in a controlled experiment with a Jeep. In this experiment, the hackers remotely controlled the radio volume and fuel transmission. Now that was a test, but then it becomes real when a live incident occurred on a 2013 Chevy Corvette – hackers were able to take control of the brakes and windscreen wipers. You may wonder what cars have to do with the network; well the car is an autonomous system similar to your firewalled autonomous enterprise network. As IoT devices interact with them, similar to how they interact with the autonomous systems of these cars, they can provide secret tunnels to intruders to hijack your network and do much more than “play with the volume controls.” For example:
- The hack of a mobile device connected to your network can lead to the compromise of company data.
- A machine-to-machine hack can lead to a serious injury or loss of life if a machine action is wrongly triggered without all the right operational or safety parameters required for such an action.
There are more eminent IoT security threats that can take your network down and compromise your business. It can even be fatal.
Network administrators must ensure that all connected devices and their data flows are genuine and authorized. They must develop a security posture that will fit the need of their organizations and scale interactions between connected devices from varying systems.

Creating standardization for security protocols for the staggering variety of IoT devices is easier said than done. In fact, not much exists in this regard. Unlike the computing and mobile devices, IoT devices do not have a universal standard of design, operating system, or function parameters making it difficult for a “one-size-fits-all” approach to protection. Traditional network security policies are no longer sufficient and have to be broadened in a bespoke manner to protect these increasing connected devices. I would advise every organization/business leader to leverage expert security support to ensure that you are well protected. You will have the double benefit of gaining assurance on the level of agility of IT systems to be #IoTReady. There are a lot to benefits from interaction in the new world of IoT where you can expand your market or gain service component from a partner’s API and other connected device information exchanges.
This heightened security concern is going to be around for a while till we begin to see some IoT standards and market maturity. All said and done it is promising that enterprises are becoming more and more aware and will demand more security from the market — 40% of enterprises indicate they will increase security by 2018; according to the Gartner report, “IoT Cyber Threat to increase Focus on Security, February 2015.”
Capacity management for the IoT:
The second critical touch point that is fundamental to every organization with IoT is the increasing amount of data, analytics and control of traffic that the networks must handle. This brings capacity management and its impact on the performance of your network front and center.

According to Cisco’s Global Index: Forecast and Methodology from 2013-2018 whitepaper, the data that is created globally by IoT devices will be 277 times higher than the data being transmitted to data centers from end user devices. This will result in 403ZB per year by 2018. Gartner indicates that – The Internet of Things (IoT) is promising to transform the data center market. And when this transformation happens, data centers will be flooded with huge amounts of data. So your network is going to have its own giant share of the pie, as it becomes a norm for all things within and outside your network needing to talk to each other over the Internet. You network too will become an engine for generating “big data.”
This “big data” must be synthesized, analyzed for business insights and stored, further creating the need for increased storage, computing and network resources. It is better that your organization is prepared for this need sooner rather than later. But how prepared are you to handle this IoT deluge?
- Do you have the capability to accurately forecast the level of connectivity and IoT interactions you network will have to manage?
- How do you size you infrastructure for scale and optimal performance?
- What areas of your network are being fully utilized today and what areas are candidates for optimization?
- What type of ongoing capacity management policies do you need to put in place?

In the era of IoT you need to approach capacity planning with more depth including the factoring of many variables introduced by IoT, Bring Your Own Device (BYOD) and machine-to-machine interactions. If you assume that Cisco’s predictions (that IoT data will be 47 times higher than total data center traffic by 2018) will have some correlation on the growth rate on the traffic your network will have to handle, then you can begin to see that ensuring you have an #IoTReady capacity management plan is smart business.
At the end of the day, the true exponential effects of how much data an IoT instance will generate is not fully established yet. This will mean capacity management tools of the future must have more Intelligence and automated capacity maintenance features.
Get #IoTReady
Start with a proper security assessment; as a result of this you will begin to get an insight into all the different pieces that connect to your network and the types of applications they introduce. Use that information as input into a capacity management plan to ensure your network has the right size and operational parameters for high performance. ExterNetworks is taking the lead to help businesses with the right security solutions and capacity planning. If you don’t have the internal expertise to spearhead this effort, reach out to ExterNetworks and we’ll get you #IoTReady.