Smart Office Needs Smart Security
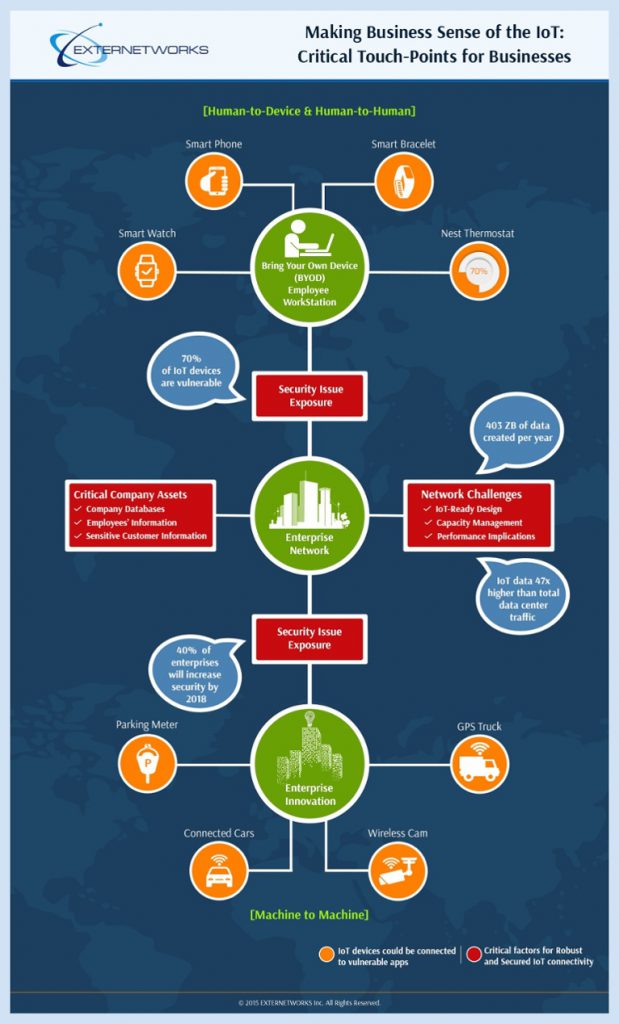
The Internet of Things (IoT) devices continue to create endless possibilities. Most of all, they have affected our everyday life – the way we eat, sleep, work, live, and commute. A potted plant can now water itself and change the temperature in your room by sensing if it is too cold or too thirsty. You can impress your clients with snazzy lighting by setting the color that matches their attire.

Connected devices now communicate with each other to improve productivity, control costs, manage inventory and reduce mundane monitoring.
Everyday lighting is now managed through sensors that turn on/off when you walk in and walk out of a room. These capabilities are still evolving and are bound to get better by the day. Devices such as printers and copiers set the precedence of connected devices in an office network. With the convergence of technologies such as Wi-Fi, Bluetooth and Internet, offices with connected devices have become smarter.
All Good Things
Things that required everyday monitoring now function on their own when you simply enable them to connect to a network. Connected devices such as security cameras, door locks, motion sensors, vending machines, light bulbs, temperature control systems and window blinds now communicate with each other to improve productivity, control costs, manage inventory and reduce mundane monitoring. This communication between connected devices is facilitated by cognitive computing systems – a dream 60 years ago – that allows you to control your environment.
The Downside
Philosophically, all good things must come to an end. But not on their own, sometimes, they are forced to. Likewise, all the good things that are made possible with IoT can crash during an attack, which may result in unintended consequences. HP found that 70% of the IoT devices are not designed to be secure. It is meaningless to attack a potted plant. But in a workplace, it could be a lack of protection from attacks, the potted plant is vulnerable and becomes an entry point that exposes your network.
Attacking entry points that are connected to the Internet not only causes huge monetary losses but also loss of life. It also provides a legitimate access to criminals, who can further create more illicit connections. The recent attacks on Chevy Corvette and Apple App Store are just a tip of the iceberg. The best (here worst) is yet to come.
Security, Security and More Security
Cyber attacks are discussed, analyzed and averted every day. In 2015, more than 548 online attacks have been recorded to date in the U.S alone. The adoption of IoT is still at a very nascent stage. As the adoption progresses, cyber attacks are only bound to increase exponentially. These attacks will affect supply chain, enterprise data and finally, productivity.
IoT device manufacturers must create robust devices for accommodating functionality and security. You must implement simple and standard security policies, coupled with the due diligence of these device manufacturers. Operating systems must be standardized; applications must be designed using best practices. Devices must be able to receive updates to correct flaws or vulnerable software.
Will You Ever Get a Secure IoT?
While IoT has opened the door to endless possibilities, adding millions of end points will add load to your network, not to mention the billions of lines of code. These devices must be detected and authenticated to allow network segmentation and implement the principle of least privilege.
IoT network security components must allow you to detect intrusions and report any anomalies. Many entities will be added to your network. Unless you are vigilant, you will not even know if you are attacked.
The final key element of IoT security is the data it generates. IoT data must be encrypted – encryption can be built into the device or in the application that interfaces with it. However, the choice of storing data must be left to the user.
These are a few basic things that must be followed to improve IoT security:
- Implement security from the beginning
- Allow updates and future-proofing
- Device authentication and access control
- Prepare for all kinds of attacks
If you can follow these practices, cybercriminals will find it difficult to attack your smart plant and penetrate your network to access it.
Related Posts: Cyber Security Infographic