21st Century Confidence Scheme: How the Increasingly Popular Social Engineering Hack Can Be Prevented
A Confidence Scheme for the Technology Age With the increasing complexity of hardware and software based cyber security, social engineering is once again gaining popularity among groups of hackers looking...
Exploring Vulnerabilities in Network Security
Do You Understand the Challenges of Network Security? In 2016, Gartner estimated that 99 percent of network security attacks were due to vulnerabilities technical professionals had identified at least one...
How to Choose the Best Cloud MSP for Beneficial Cloud Adoption
Technology-enabled services in an on-demand, cost-effective, secure, and quick manner are a must in today's business landscape. The need for such a service at will has given rise to the...
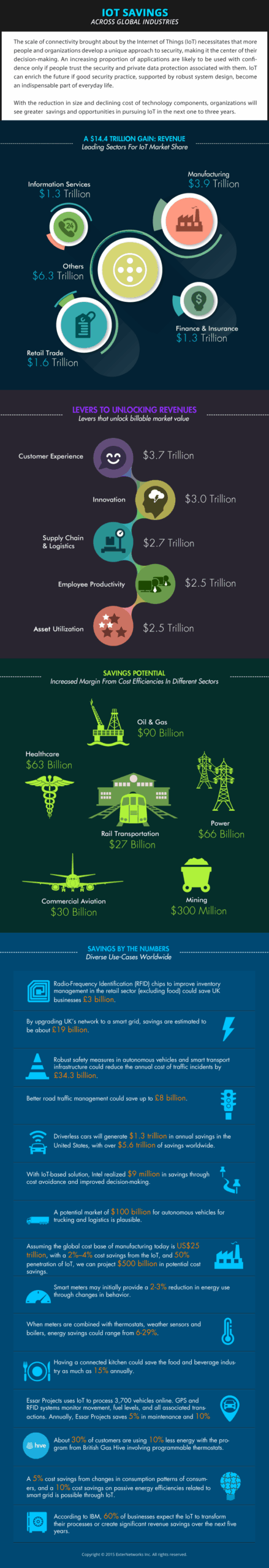
IoT Savings Across Global Industries -Infographic
The IoT connects computer networks, machines, actuators, sensors, and devices globally; and blends the physical world with the virtual world of the Internet and software. It enables companies and consumers...
Preventing Cyber Attacks Through Efficient Cyber Resilience
Today's business world requires companies to use a broad range of technology and IT equipment, the Internet, as well as mobile devices for conducting business. Hence, it is natural that...
Is Your Anti-virus Giving You a False Sense of Security?
Security management is indisputably important for any company today. Threats to security has led to an inevitable adoption of anti-virus software by most if not all organizations and with good...
Smart Office Needs Smart Security
The Internet of Things (IoT) devices continue to create endless possibilities. Most of all, they have affected our everyday life – the way we eat, sleep, work, live, and commute....
VTech hack Exposed Children’s and Parents’ data
In a recent data breach on a kids toy-maker, VTech, 6.4 million children’s data including photos, first names, genders, birth dates and home addresses, as well as information of...
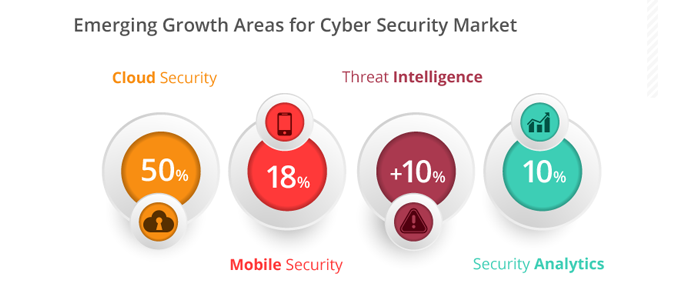
Cyber Security Infographic
Today, every business needs the cyberspace to thrive and the battle to hijack your systems is constant in this realm. Hence, no one is really 100% secure with a...
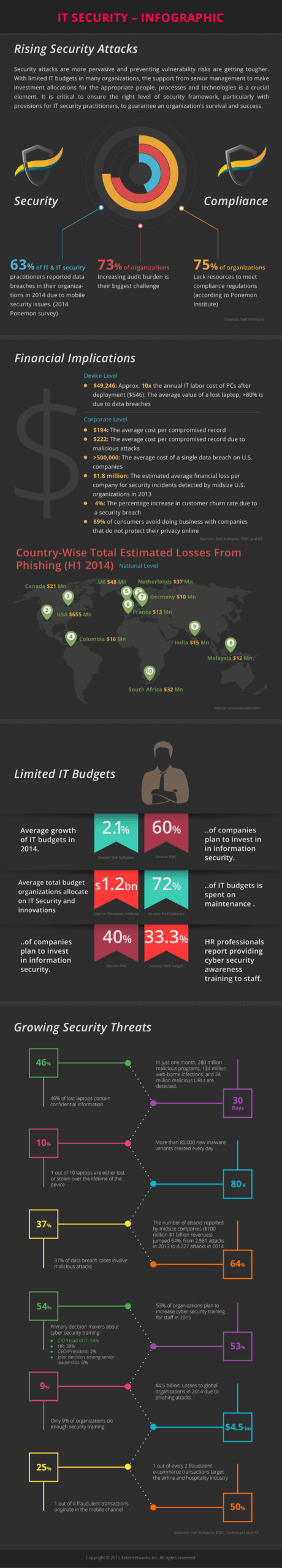
IT Security Infographic
Cyber viruses and IT threat are continuously evolving at this time, when we want to do all things in the cyberspace. It is for this reason that you should always...
Cloud Adoption is Accelerating – Where Do You Stand?
Cloud adoption is no more a matter of if, but what and when. Many organizations have realized and experienced its vast benefits such as business agility, scalability, flexibility, and ROI....
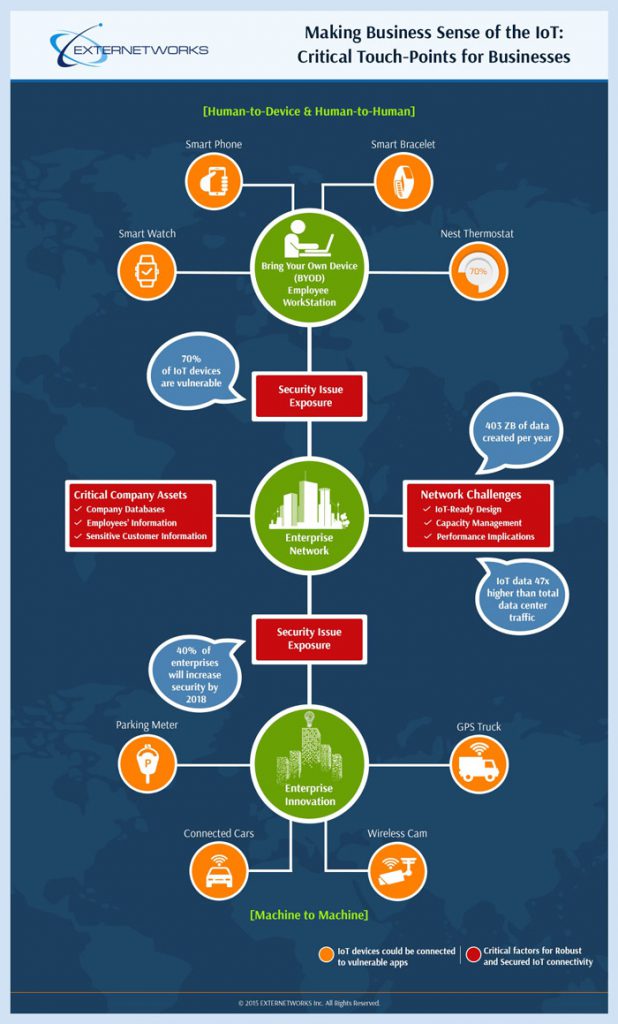
Critical Touch Points of IoT
The Internet of Things (IoT) is fast becoming a household name, as it is the next big area of development in the global technology landscape. Businesses need to take the...
How To Get 24X7 Support And Increased Output By Outsourcing
Years ago, businesses had to build their own software applications according to the tasks that they needed to carry out. However, thanks to SaaS, they can now easily adopt outsourced...
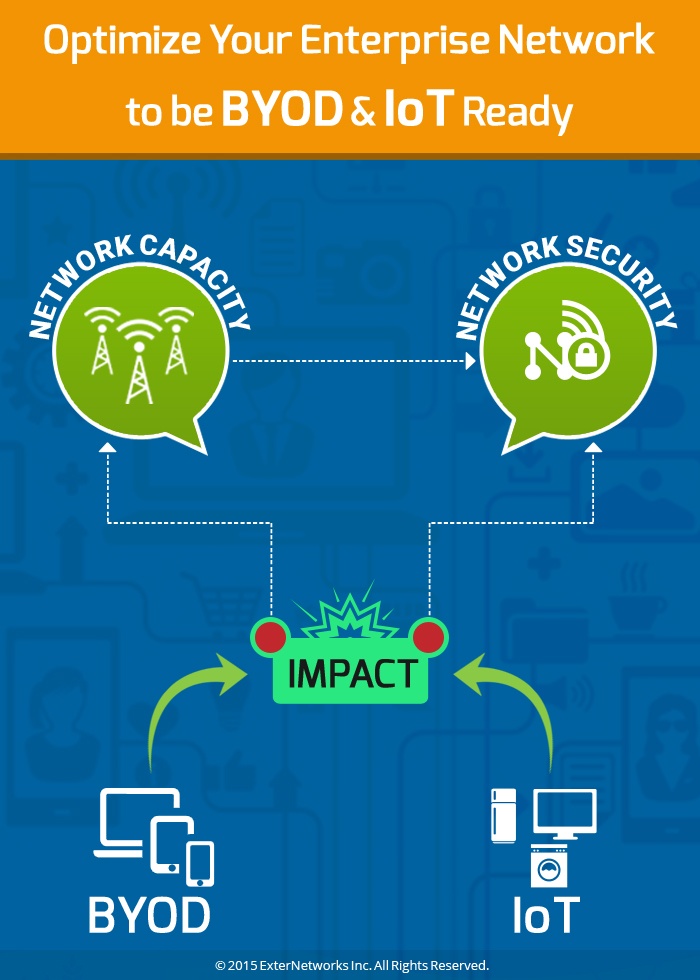
Optimize Your Enterprise Network to be BYOD and IoT-Ready
With the advent of the Internet of Things (IoT) and ‘Bring Your Own Device’ (BYOD) culture, your enterprise network is sure to face a different set of challenges and roadblocks...
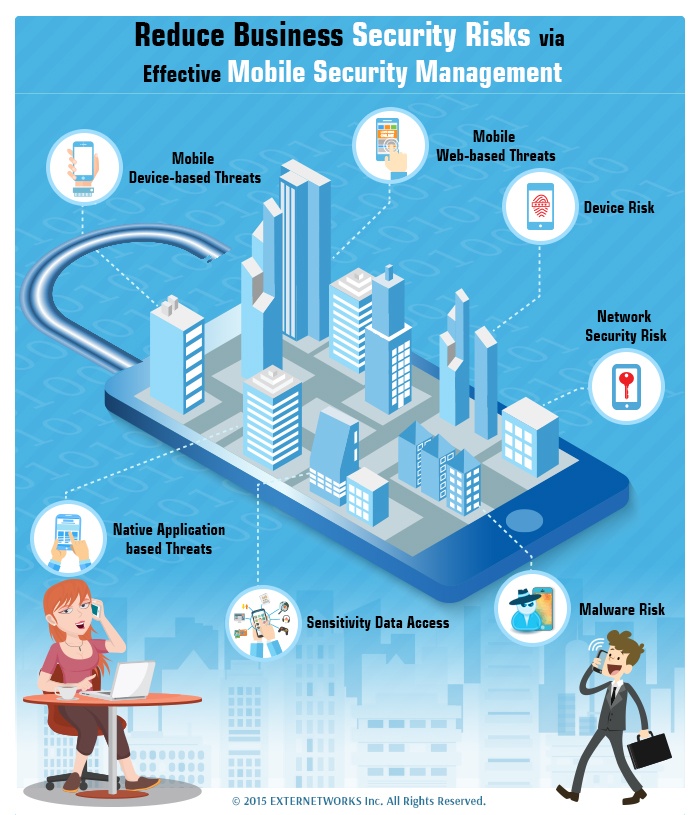
Reduce Business Security Risks via Effective Mobile Security Management
Today, businesses know that they have globally dispersed partners, distributors, and even customers. To keep up pace with the changing conditions of how business is conducted today, more and more...
Data Center Optimization to be IoT-Ready
Technology, which connects everything, has become an inherent part of our lives. These connections have immensely helped organizations to enhance the quality of service to their consumers. As the technology...
Implications of the Internet of Things
With the explosion of connected devices and the massive amounts of data they produce, businesses, individuals, government bodies as well as IT staff need to evaluate their current strategy and...
How to Make Business Sense of the Internet of Things (IoT)
The fundamental need for which a business will adopt new technology is often lost amongst the hype. It can be boiled down to two basic measurable business objectives: To...
Value Proposition and Strategic Partnership through MSP 2.0
Managed Services has seen a tremendous growth in the past three years. Organizations today, whether big or small, have realized the benefits of letting an expert Managed Services Provider (MSP) monitor and...
Timely Resolutions to Avert Untimely Network Failures!
Has your network ever experienced untimely network failures? Such untimely network failures can leave any organization, and especially the IT Manager, highly frustrated and helpless. Such failures make you realize...
Leverage IoT Technologies to Sustain Competitive Business Advantage
The competition is heating up, as more and more industry giants, such as Google, Samsung, Apple and Microsoft, are entering into the IoT market with large investments to develop their...
Business Continuity Through Managed Network Services (MNS)
If you are a technology manager, you know that we work hard to manage the issues associated with networks. You are at risk every time your company is exposed to...
8 Reasons to be Smart About Your Web App Development
Custom and Cross Platform Web App Development is growing at an exponential rate. The demand for creating customer-centric applications is outpacing the ability to meet the supply, since more developers...
4 Changes to Your IT Policy Critical for SaaS Cloud Adoption | ExterNetworks
Migrating to the cloud opens up a gamut of benefits, but the transition can be a tad challenging. To ensure the transition is both smooth and successful, you need to...
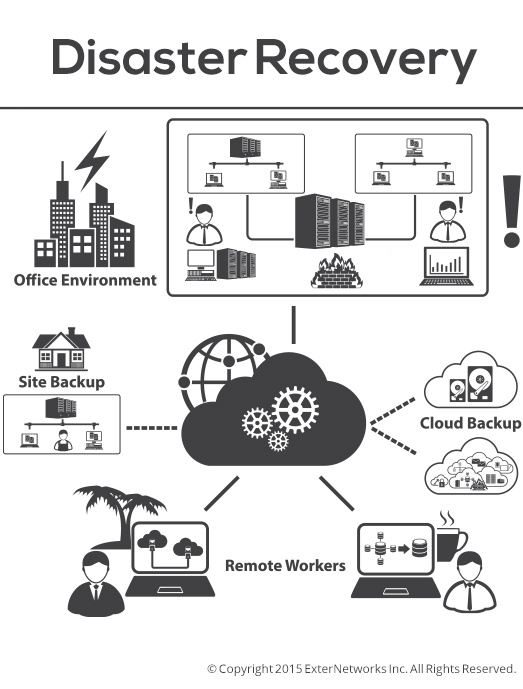
What is Your IT Disaster Recovery (DR) Plan? How Frequently Do You Perform DR Drill Tests?
Without a Disaster Recovery (DR) plan, your organization is at exceptional risk of loss of business, hacking, cyber-attacks, loss of confidential data, and more. Your DR plan can prolong your...
Internet of Things (IoT) – The Next ‘BIG’ Investment Destination
With the IoT emerging as the next big destination for investment, many industry giants are scrambling and fiercely competing to grab their share of the revenues in the IoT market....
Which Is The ‘Right’ Recruitment Agency For You?
As a job-seeker, one is always in a quandary as to which is an effective staffing agency and which is not! With an influx of too many ineffective staffing agencies...
IoT & WEARABLE TECHNOLOGIES – THE FUTURE
How They Will Reshape the Enterprise IT Landscape With the recent launch of Apple Watch and more wearable technologies to follow, more and more connected devices are expected to get...
Cyber Gang Robbed 100 Banks Worldwide – Did They Even Breach The US Banks?
Hackers have always targeted customer bank accounts but now, a cyber-gang known as, Carbanak, is stealing directly from banks, totalling over a billion dollars so far. How hackers have breached...
IoT: How Secure are You With the Internet of Things? Externetworks
Increasing network security breaches and cyber-attacks make proactive and regular security audits a critical priority for CIOs, Information Security Officers, and Network Managers. As the Cloud and the Internet-of-Things (IoT) make it...
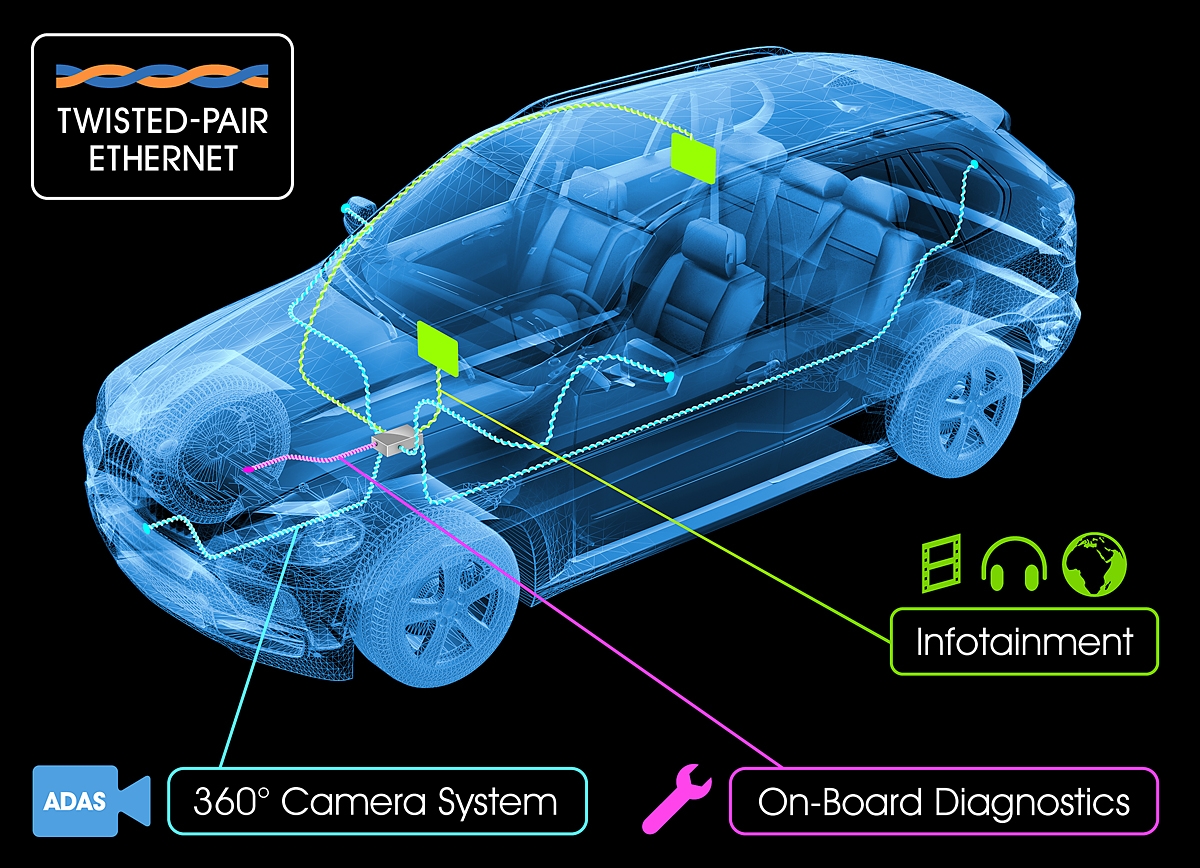
In-Car Internet Lets You Stay Flawlessly Connected to The IoT
With just a pair of Ethernet cable, you can get in-car internet, which connects to infotainment, cameras, wifi and in fact to each piece of electronic which supports network connectivity....